A registry is a database that Windows uses to store computer configuration information. Windows XP, unlike its predecessors, has no restrictions on the size of the registry.
To edit the registry in Windows there is a program Registry Editor (.. \\ windows \\ system \\ regedit.exe) You can run it by typing in command line regedit. All changes made in the registry are saved automatically when you exit the program
The registry contains information that Windows constantly accesses during operation, namely:
- profiles of all users;
- data on established programs and types of documents created by each program;
- property values \u200b\u200bfor program folders and icons
- configuration of equipment installed in the operating system;
- data on used ports.
The registry has a hierarchical tree structure consisting of sections, subsections (this is what we see on the left, opening the registry editor), and keys (what we see on the right, highlighting a section or subsection of the registry)
Registry Windows XP consists of the following main sections:HKEY_CLASSES_ROOT (HKCR) - The information stored here provides the launch of the necessary program when opening a file using Explorer. This section contains links between applications and file types, as well as information about OLE.
HKEY_CURRENT_USER (HKCU) - The settings stored here correspond to the current, active user who has logged in. This section is a reference to a specific subsection of the HKEY_USERS bush. All changes in the sections, subsections, and keys of the HKEY_CURRENT_USER bush are automatically immediately displayed in a specific subsection HKEY_USERS corresponding to the active user
HKEY_LOCAL_MACHINE (HKLM) - This section contains settings that are valid for all users of the computer. It contains information about the hardware configuration and installed software.
HKEY_USERS (HKU) - This section also contains settings for all computer users.
HKEY_CURRENT_CONFIGS (HKCC) - This section contains information about the settings of the equipment used by the local computer when starting the system, i.e. contains information about the current configuration.
All of the above sections are standard and cannot be deleted or renamed.
By default, Windows XP stores registry keys in the following files:
- .. \\ windows \\ system32 \\ config \\ SAM - HKEY_LOCAL_MACHINE \\ SAM- .. \\ windows \\ system32 \\ config \\ Security - HKEY_LOCAL_MACHINE \\ Security
- .. \\ windows \\ system32 \\ config \\ Software - HKEY_LOCAL_MACHINE \\ Software
- .. \\ windows \\ system32 \\ config \\ System - HKEY_LOCAL_MACHINE \\ System, HKEY_CURRENT_CONFIG
- .. \\ windows \\ system32 \\ config \\ Default - HKEY_USERS \\ .DEFAULT
Section Related Files HKEY_CURRENT_USER stored in folder .. \\ Document and Settings \\ Username \\ .. You can view all stored registry files and their location here: HKEY_LOCAL_MACHINE \\ System \\ CotnrolSet001 \\ Control \\ HiveList \\ At booting windows refers to this section to initialize all the main registry keys.
One incorrect change in the registry can disable the operating system. Use the following tips:
- Before making changes to the registry, do backup the section or subsection you are about to make changes
- Do not replace the registry Windows XP registry of another version of operating systems Windows or Windows NT
- Never leave the registry editor unattended
To back up the subsection that you want to change, select the subsection, right-click and select Export. Choose a place and a name for the file (the name can be arbitrary, but it is better that it matches the subsection, so you will not forget what the file is; the extension must be * .reg) and click the Save button. Now, if after making the changes, something will not work correctly, and you forget that you changed, just open the saved file, respond positively to the request for changes to the registry and the previous value will be restored. This method Only suitable for backing up a subsection.
To create a backup copy of the entire registry, you can use the Data archiving program (Start - All programs - Standard - Utilities - Data archiving). To do this, run the Data Archiving program on behalf of the administrator, enter the advanced mode, select the Archiving tab. In the left window we find and mark the line "System State". Below we select the location and name for the archive file. Press the archive button, go to the Advanced tab and uncheck Automatically archive protected system files along with the state of the system. Click OK, then Archive. The size of the archive will be about 20-25 MB. You can also restore the registry using the backup program.
Today we move on to the lessons of the "Advanced user" level, and begin with an introduction to the Windows registry.
Many have heard, but not everyone knows, "what is the registry in the computer", now we will fix this defect.
System registry, or registryWindows Is a database for storing settings operating system, installed programs, user and equipment parameters, in addition, information about computer devices (configuration) is stored in the registry.
That is, this is the place where most of the settings on your PC are stored.
Example: You have changed the desktop wallpaper, information about this is recorded in the Windows registry. At the next boot of the operating system, the data will be read from the registry, and the desired picture will be displayed on the desktop.
The registry is available in all modern (and not so) operating systems of the Windows family: 10, 8, 7, XP.
Why should a user know about the registry?
You can ask, « why do I need a registry if all the settings can be changed through the control panel and program parameters?»
Indeed, most of the settings can be changed using the familiar graphical interface (in various "menus" check the boxes and click "OK"). But not all settings are accessible in the usual way.
Some settings can only be changed by editing the registry..
What is the Registry Editor and where is it located?
To view the settings in the registry and change them, you can use a special program called " Registry Editor».
This program is located in windows folderthe file is called regedit.exe

The file "regedit.exe" is located in the Windows folder
But in the Start menu there is no shortcut to launch the registry editor! This is done for a reason. The fact is that erroneous changes in the system registry can lead to computer malfunctions, so the manufacturer hid the opportunity quick start Registry Editor (but you won’t stop us so easily 😉).
How to open registry editor in Windows?
Details on how to open the registry editor in each version of Windows (10, 8, 7, XP), I described in this article:
The fastest way to start the registry editor
I will reveal the most quick way launch the registry editor, which is relevant for all versions of Windows:
- Press on the keyboard Win +R (hold down the Windows key and, without releasing it, press the R key);
- In the "Run" window, type the command " regedit"(Without quotes) and press the button" OK»;
- If prompted, confirm the start of the registry editor with the "Yes" button.

For example, two more ways to start the registry editor can be seen in this video (for example, Windows 10):
Windows registry device
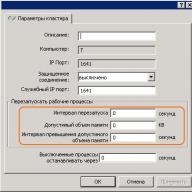
When you open the registry editor, you will see a window very similar to explorer:

Registry Editor Window in Windows 10
On the left sidewindows are registry keysthey are also called " keys"(Similar to folders ), on the right side windows are displayed parameters (similar to files) and their meanings.

Example: in the section "HKEY_CURRENT_USER \\ Control Panel \\ Desktop" there is a parameter "Wallpaper" (desktop wallpaper), the image shows that its value is "D: \\\\ Documents \\\\ Wallpaper \\\\ 09.jpg". Thus, a picture is registered, which is displayed as the desktop background.
Parameters can be of different types., in the image below I gave an example of all possible parameters for Windows 10 and 8 (for clarity, the parameter name corresponds to its type):

Types of registry settings in Windows 10 and 8 (example)
Changing the values \u200b\u200bof the parameters just produce changes in settingsWindows and programs. Sometimes it is necessary to create new parameters of a certain type in order to get a new opportunity in the program or operating system. But this is the topic of the following lessons (the first examples can be seen on the links below).
In more detail about the registry device, I can write a separate IT lesson, if interested - write in the comments.
Examples of using the registry to restore Windows
Naturally, I did not just raise the topic of the Windows registry. When solving problems, one often has to resort to editing the settings by changing registry settings.
And a little warning:
Take your time to change something in the registryif you don’t know what the setting affects. Before making changes, back up the registry subkey to be modified.
Conclusion
So, today we answered the question "What is the registry in the computer." That is, they learned what system registry Windows (10, 8, 7, XP), met with registry Editor and learned how to open it (remember the easiest way with the keyboard shortcut Win + R?), even briefly got acquainted with registry device and reviewed examples of its useful use.
The registry topic is quite extensive, with it you can do a lot, but today there were so many new information, I’ll leave the most interesting next time.
Do you want to continue? Write in the comments!
Of course, I'm waiting for your questions, suggestions and reviews.
Copying prohibitedbut you can share the links.
If the operating system was installed on the computer for a long time and during all this time it has never been reinstalled, then users, as a rule, note a decrease in the speed of its operation and the occurrence of periodic failures. This can be manifested in slow loading, long opening of some programs, in the appearance of dialog boxes about errors that have occurred. And than longer person works at the computer, the more glitches and malfunctions he notices, and over time, working on such a computer can turn into a real nightmare.
The culprit of all these listed problems can be the registry - a very important component of the operating system. Therefore, it would not hurt even novice users to know its purpose, impact on the overall operation of the OS, as well as the means of monitoring and caring for it.
So sooner or later, the user is faced with the question - either reinstall the operating system with all programs and re-configure it user interface, or try to “clean” the system and restore its former performance.
DESCRIPTION AND PURPOSE
The Windows registry is essentially a tree-like database that contains information about all the parameters that are required for the correct and uninterrupted operation of the operating system. It contains settings for the installed hardware and software, personal profiles users with access to a computer, the types of files that programs can create, as well as information about the properties of folders.
The value that the Windows registry has is difficult to overestimate. How correct his information is depends on how efficiently all PC nodes will work, both software and hardware. If the user begins to notice any problems in the operation of his computer, then this is a clear sign that the registry has failed and some of its settings have gone wrong. If a malfunction in the system registry has occurred, the user will not be able to load Windows and the operating system will have to be reinstalled.
The registry is stored at X: \\ Windows \\ System32 \\ config, where X is the letter of the system drive.
ROOT SECTIONS OF THE SYSTEM REGISTER
The Windows registry consists of several main sections:
- - HKEY_CURRENT_CONFIG (HKCC) - the section contains all the information about the hardware profile that is used on the local machine during system startup;
- - HKEY_CURRENT_USER (HKCU) - the section stores information about a specific user who has logged into the system and is currently working in it. This folder stores its folders, screen settings, and settings for the control panel;
- - HKEY_CLASSES_ROOT (HKCR) - the section contains data on file type extensions and applications that will open when they start;
- - HKEY_USERS (HKU) - this branch stores information about all loaded active user profiles of a particular PC;
- - HKEY_LOCAL_MACHINE (HKLM) - a branch for storing information about loading Windows OS, information about device drivers and computer hardware;
- - HKEY_USERS (HKU) - the branch stores individual profile settings for each user who is registered in the system. Information about the default profile for new users being created is also stored here.
Each root registry key contains many subkeys, which in turn can already have their own multiple subkeys in which system parameters are stored. The registry hierarchy is very complex, and the number of sections in it is simply huge, therefore, within the framework of this material, we just need to understand the very principle of building its structure so that if necessary you could find the parameter you need.
INFLUENCE OF THE REGISTER ON WORKWINDOWS
As noted earlier, the speed of the system and its stability directly depends on the state of the registry. Most often, the system begins to "slow down" when the registry increases in size. And the larger it is, the longer the computer boots up, since when the OS starts, the system registry is always checked for errors, after which a backup copy is made. Moreover, the more software costs on the computer, the larger the registry becomes.
At the same time, Windows is so arranged that the work of any software, whether it is a simple utility or a super game, will always require interaction with the system registry to find the necessary parameters, which are becoming more and more difficult to find, the larger the registry size and the number of branches in it.
There is another important factor affecting speed. work windows, but before telling about it, we will make a small remark. In computers, there are two main types of memory - RAM (random access memory), it is also random access memory, and ROM (read-only memory), which include hard disks, flash drives and other components that store your data. RAM is a very fast memory that allows you to instantly exchange information with the central processor, but ROM works much slower.
Now, we continue, the slowdown in opening programs is very often caused by the fact that there is not enough random access memory. And often, in order to provide the necessary amount of memory for some program, the system gets it out of its total volume (combination of RAM and ROM), starting to access the hard drive space, i.e. the so-called “swap” occurs (part of the information is recorded on hDD) As a result, when the application is loading or running, it needs the necessary information written to disk, it is read much longer than if the system took them from the RAM.
To prevent such a situation, it is necessary to exclude the ingress of all unnecessary or rarely used programs in the RAM.
But the fact is that one of the main sources of garbage "RAM" on your computer is the registry, the data from which, windows system loads, at startup, without knowing whether you will need them or not. Among them, there may be "traces" for a long time remote programs, applications or their parameters that you are unlikely to need. Thus, if you do not pay due attention to the state of the system registry, all this garbage will clutter up a precious place in RAM.
Very often, during the operation of the computer, dialog boxes begin to appear before users with all kinds of errors that occur in Windows. Many of them are the result of incorrect changes made to the registry that conflict with the system settings. This can happen due to the replacement of standard libraries with older versions or after their sudden removal, for example, after a virus infection and subsequent cleaning of the computer.
REGISTRATION METHODS
The user can solve all problems with the "bloated" registry in two ways: manually or using programs, but in any of these cases, changes will be made to the system registry.
Inexperienced users do not need to make changes manually. In this case, it is better to use special programs with which you can change the registry database painlessly for the OS to work. The benefit of such utilities is now enough on the market, while there are both paid programs and free ones, with quite decent functionality. The main purpose of these utilities is to search and delete bad keys that are no longer in use, but only clog the registry, as well as defragment it.
And yet, if you decide to make changes to the registry yourself, then the most optimal solution would be to use the built-in Windows utility Registry Editor. In order to get the registry editor, there is a special command “regedit”, which must be entered in the Run window (called by clicking windows keys+ R).

By running the utility, the user will see a window divided into two parts, in one of which sections, subsections and branches of the system registry are displayed, and in the other - the parameters of the element that the user selected in the registry.

Also in the registry editor, on the Edit tab, there is a search option (called by pressing Ctrl + F) that searches for given words in the section names, parameter names and their values. This is a very convenient feature that allows, for example, to clear the registry of traces unnecessary program by her name.
Correcting the registry manually, you need to be very careful. One wrong action and system performance will be broken permanently, and Windows will have to be reinstalled.
Users who are just starting to understand how to use a computer often ask when they can make changes to the registry themselves, and when they need to contact a professional for help. If possible, a specialist, if there are problems with the registry, you should always call or at least invite an experienced acquaintance. It is highly undesirable for a layperson to make adjustments to valid entries. In addition, before updating it is necessary to make a backup copy of the registry, then in case of improper actions that will lead to the system not working, it will be possible to restore the registry from backup through the same utility that was used to make the changes. You must also remember that in no case can you replace the registry of one version Windows system registry of a different version.
The most common errors and their consequences when the registry is adjusted by amateurs can be called deleting or changing the necessary sections and keys, after which some programs may stop working, not loading account user or happen complete rejection system operation.
REGISTER MONITORING
The Windows registry is a reflection of the operating system. And in order to understand that everything in the system works without interruptions, it is necessary to conduct its constant monitoring. The ideal option is to use for monitoring some popular utility that was created specifically for this purpose. Why do I need to install and use it? In order to analyze the work of programs. The user will always be able to see which processes are occurring in the system, which programs are running and which of them most often access the registry, and if he sees something suspicious, he will be able to take measures to eliminate it.
Monitoring utilities are fairly easy to use. Even a person who does not have a special education can understand them. And this is their big plus, since to know at least approximately what is happening in the registry of the OS of their computer, it is desirable for all users, both experienced and beginners. For example, you can use one of the most popular registry monitoring utilities - Registry Monitor (RegMon).
CARE OF THE REGISTER
By installing and then removing various programs, a Windows user does not always know that, as a rule, information about them is not completely deleted from the registry. There are always some “tails” that further slow down the system. To prevent this from happening, it is necessary not only to monitor the registry, but also to provide care for it. To do this, you do not need to look for the remaining entries in the registry yourself, you can do this using special programs, the existence of which was already mentioned above. The jv16 programs PoverTools, CCleaner, Reg Organizer, RegCleaner and others cope well with this work. With their help, the user can not only clean the registry from “garbage”, but also defragment the hard drive, edit startup, clear browser history, delete obsolete files to restore the system, etc.
CONCLUSION
The ability to handle the registry is a huge plus for a user of any level. In this case, without waiting for outside help, you can independently improve or restore the operability of your operating system in case of serious problems. True, it’s even more important not to bring your working operating system to a deplorable state by monitoring the registry or at least constantly cleaning it from “garbage”.
In general, most of the problems with Windows that arise due to registry problems can be resolved independently with the help of expert advice, which they favorably post on the Internet. True, in order to use them, in any case, you should at least in general terms know what the registry is and how to make changes to it. Well, if you yourself could not cope with the problems that arose, your basic knowledge will help to correctly explain the essence of the problem to a computer service specialist, which will significantly speed up the process of eliminating it.
Among the sources of malware penetration, the most dangerous are:
1. Internet
The global information network is the main source of the spread of any kind of malware. Malicious software can get onto the computer during the following user actions:
- When visiting a site containing a malicious code. An example would be drive-by attacks. Drive-by attack is carried out in two stages. First, the user is lured with the help of spam ads distributed by e-mail or placed on a bulletin board on the Web, to a site containing a code that redirects the request to a third-party server on which the exploit is stored.
In drive-by attacks, cybercriminals use exploit kits that can target web browser vulnerabilities, plug-ins, vulnerabilities in ActiveX controls, or vulnerabilities in third-party software protection. The server hosting the exploit kits can use the data from the header of the HTTP request of the visitor’s browser to determine the version of the browser as well as the operating system. As soon as the victim’s operating system is determined, the corresponding exploit from the set begins to act / is activated. In the event of a successful attack, a Trojan is installed on the computer invisibly to the user, which provides attackers with complete control over the infected computer. Subsequently, they gain access to confidential data on such a computer and the ability to carry out DoS attacks from it.
Previously, attackers created malicious sites, but in lately hackers began to infect law-abiding web resources by placing scripted exploits on them or code to redirect requests, which makes attacks through the browser even more dangerous. - When downloading malware from sites that masquerade as keygens, crack, patches, etc.
- When downloading via peer-to-peer network (for example, torrents).
2. Email
Mail messages arriving in the user's mailbox and stored in mail databases can contain viruses. Malicious programs can be found both in the attachment of the message and in its body. When you open a letter, while saving the file attached to the letter to disk, you can infect the data on your computer. Also, mail correspondence can become a source of two more threats: spam and phishing. If spam entails mainly a loss of time, then the purpose of phishing emails is your sensitive information (for example, credit card number).
3. Vulnerabilities in software
So-called “holes” (exploits) in software are the main source of hacker attacks. Vulnerabilities allow a hacker remote access to your computer, and therefore to your data, to the resources available to you local area networkto other sources of information.
4. External storage media
For the transfer of information are still widely used removable drives, memory expansion cards (flash), as well network folders. Running any file located on external media, you can infect the data on your computer with a virus and, imperceptibly, spread the virus to your computer's disks.
5. Users
Trusting users themselves install seemingly innocuous programs, thus infecting their computer. This method is called social engineering - virus writers get the victim to install malicious software using various tricks.
6. How to eliminate the possibility of infection
To exclude the possibility of computer infection, install a trial version of one of the products: Kaspersky Anti-Virus, Kaspersky Internet Security, Kaspersky Total Security. After installing the program, update the anti-virus databases and run a full computer scan.
About viruses: Types of known threats
About viruses: Signs of a computer infection
There are a number of signs that indicate a computer infection. If you notice that strange things are happening to your computer, namely:
- unexpected messages, images and sound signals are displayed on the screen;
- the tray of the CD-ROM device suddenly opens and closes;
- randomly, without your participation, any programs are launched on your computer;
- the screen displays warnings about an attempt by any of the programs on your computer to access the Internet, although you did not initiate such a behavior in any way,
then, with a high degree of probability, we can assume that your computer is infected with a virus.
In addition, there are some characteristic signs of a virus infection via mail:
- friends or acquaintances tell you about messages from you that you did not send;
- in your inbox is a large number of messages without a return address and header.
It should be noted that such signs are not always caused by the presence of viruses. Sometimes they can be the result of other reasons. For example, in the case of mail, infected messages may be sent with your return address, but not from your computer. There are also indirect signs of a computer infection:
- frequent freezes and malfunctions in the computer;
- slow computer operation when starting programs;
- the inability to load the operating system;
- disappearance of files and directories or distortion of their contents;
- frequent access to the hard drive (the light on the system unit often blinks); Windows to store computer configuration information.
- profiles of all users;
- data on installed programs and types of documents created by each program;
- property values \u200b\u200bfor program folders and icons
- configuration of equipment installed in the operating system;
- data on used ports.
- Before making changes to the registry, make a backup copy of the section or subsection in which you are going to make changes
- Do not replace the registry Windows XP registry of another version of operating systems Windowsor Windows NT
- Never leave the registry editor unattended
Windows XP and Windows Vista unlike its predecessors, it has no restrictions on the size of the registry.
The registry contains information to which the operating system family Windows constantly appeals during work, namely:
The registry has a hierarchical tree structure consisting of sections, subsections (this is what we see on the left by opening the registry editor), and keys (what we see on the right, by highlighting a section or subsection of the registry).
How to work with the system registry?
One wrong change in the registry can disable the operating system! Strictly follow the instructions of viral analysts Kaspersky Labs when editing \\ changing the registry!
When editing / modifying the registry, use the following tips:
Before editing and making changes to the system registry, back up the registry!
In some cases, in order to treat a computer infected with a virus and / or eliminate the consequences of a computer infected with a virus, it is necessary to edit / make changes to the system registry of the operating system of the family Windows About Viruses: Cure Utilities
Windows registry, or system registry - a hierarchically built database of parameters and settings in most operating systems Microsoft Windows.
The registry contains information and settings for hardware, software, user profiles, presets. Most of the changes in the Control Panel, file associations, system policies, the list of installed software are recorded in the registry.
The Windows registry was introduced to streamline the information previously stored in a variety of INI files, to provide a single mechanism (API) for writing and reading settings and eliminating short name problems, lack of differentiation of access rights and slow access to ini files stored on the file system FAT16, which had serious performance problems when searching for files in directories with a large number of them. Over time (finally - with the advent of file system NTFS) the problems solved by the registry disappeared, but the registry remained due to backward compatibility, and is present in all windows versionsincluding the latter. Since there are currently no real prerequisites for using such a mechanism, Microsoft Windows is the only operating system in use today that uses the registry mechanism of the operating system. In general, the Registry is a rudiment.
Windows registry in its current form.
The registry in the form as it is used by Windows and as its user sees in the process of using the programs for working with the registry is formed from various data. To get what the user sees when editing the registry, the following happens.
Initially, during the installation (installation) and windows settings, files are formed on the disk in which a part of the data regarding the system configuration is stored.
Then, during each boot of the system, as well as in the process of each entry and exit of each user, a certain virtual entity is formed, called the "registry" - the REGISTRY \\ object. The data for the formation of the “registry” is partially taken from the very files (Software, System ...), partially from the information collected by ntdetect at boot (HKLM \\ Hardware \\ Description).
That is, part of the registry data is stored in files, and part of the data is generated during the boot process of Windows.
To edit, view and study the registry standard windows tools (regedit.exe and regedt32.exe programs) registry branches are available. After editing the registry and / or making changes to it, these changes are immediately written to files.
However, there are third-party programs that allow you to work directly with files.
Registry optimization programs, tweakers, as well as installers and uninstallers of programs work through special functions of working with the registry.
Where are the windows registry files?
The registry files are in the windows \\ System32 \\ config \\ folder, there is still a user registry key in the% userprofile% \\ ntuser.dat file.Backup copies of registry files are located in the windows \\ System32 \\ config \\ RegBack folder.
What are the main sections (bushes) of the registry?
HKEY_CLASSES_ROOT Section
This is the main Windows registry key; it contains file associations that associate file types with programs that can open and edit them, and class registration for Component Object Model objects (COM - a component model of objects). The latter provides an opportunity to change an incredible number of rules of system behavior - you should not do this without a good reason.
Section HKEY_CURRENT_USER
It stores the settings of the currently active user. The branch stores user folders, various personal settings and control panel settings. This information directly interacts with the user profile. This branch consists of several subsections that contain the paths of sound files used to sound system events; various data that can be changed in the control panel, for example, the arrangement of icons; information about the current keyboard layout, user settings for applications, etc.
HKEY_LOCAL_MACHINE Section
Here are stored configuration parameters that apply to this computer (parameters are set simultaneously for all users). For example, it contains information about the computer configuration, installed drivers and programs, port names, file system settings, etc.
HKEY_USERS Section
This branch contains information about the profiles of all users this computer (username, desktop settings, etc.). This section also stores the default settings for the desktop, the Start menu, etc. They are needed when a new user logs in for the first time. At this point, the default settings are copied to his profile, and all further changes made by the user will be saved in this branch.
Section HKEY_CURRENT_CONFIG
The key is responsible for Plug & Play devices and contains information about the current configuration of a computer with a variable composition of devices, such as flash cards, printers, faxes, external drives etc. This section also contains information about the current profile of the equipment that the computer uses when starting the system.
HKEY_DYN_DATA
This section is available only in the registry of the Windows 9x / ME family of operating systems. Contains dynamically changing data about the computer (processor load, swap file size, etc.)
How to edit the registry?
Everything is simple in windows search we recruit regedit and run the registry editor as administrator. Before performing any operations in the registry, you must make a backup! If something goes wrong, you can return to the working version of the registry.
Optimization of the registry.
There is debate about whether to optimize the Windows registry. I would say so for more weak computers optimization is more useful than for powerful ones. But there is one more nuance, sometimes not cleared registry settings can cause crashes and conflicts of software and hardware, therefore I recommend doing registry cleaning of unnecessary data.
In addition, the registry is fragmented over time, this is also due to cleanings. Therefore, those who do registry cleaning constantly, I also recommend sometimes doing registry defragmentation.
To optimize the operation of the Windows registry, you can use programs, WinOptimizer, Reg Organizer, Auslogics Boostspeed.
If you have questions, watch the video above.