Why do I need to clear the free space? hard drive computer?
There are several practical reasons that explain the need to remove free space on a personal computer. If you leave the office, of course, you will want to delete all personal and confidential files on your office computer. If the management of your company is going to upgrade computers, then again there is a need to delete important corporate files from the hard drive that may contain sensitive personal and professional information. The problem is that not all people know that simply deleting files on the Windows operating system is not enough.
This means that all data on the hard disk is immediately and permanently unreadable. Encryption hard drives can transfer ownership and control of your active hard drive protection using passwords, fingerprints, or other authentication means.
Allow changes to the computer during the boot process, and accept the license agreement. Make sure to select right hard disk. If you do not see this option, make sure that you are dealing with a self-encrypting drive. Note. The dialog box is temporarily closed. Now hDD it is reset to the factory settings, and all data on the hard drive is not constantly read. Thus, the hard drive can be safely removed, reused, repaired or returned with an expired lease.
If you permanently delete files on your computer, then you may notice that sometimes some of the deleted files reappear on your system. This is no coincidence. In fact, when you delete files from the operating room windows systems, you may not see them, but in reality, they will still be saved on your hard drive. In this regard, it becomes clear why it is necessary to clean the free space of your personal computer.
Users may ask: why do I need to clear the free space on my computer’s hard drive? What will it give? As noted above, personal and confidential information could be stored and then deleted on a personal computer. Even after the deletion, and you can not even guess about it, the deleted files usually remain on the hard drive. Even if you empty the Recycle Bin, the files will still remain in the computer’s memory - in the part where it will not be easy for you to find them.
The problem is that there are many programs on the market today designed to recover and locate deleted files. Thus, anyone with access to your computer can easily recover both personal files and all your sensitive business information. Currently, great attention is paid to the confidentiality and security of information. Your computer may contain data regarding trade transactions, personal secrets and other personal information. Remember that anyone can take advantage of all your information, and its privacy will be compromised if you do not delete them from your computer once and for all. You need to be sure that people who will have access to your computer will not be able to recover and find information that you have already deleted from your computer’s hard drive.
To clean free space in your computer you need to install a program to delete files. Such computer applications will effectively clean all files and information that you have already deleted from your personal computer. If the files are cleaned with a special application for deleting files, then none of the programs for recovering and finding files can find them.
Thus, if you will use special programsaimed at deleting files, you can be 100% sure that no one can find the secret and personal files that you deleted and use them in order to cause you trouble. And best of all, file removal programs are available at an affordable price, so you don’t have to spend a lot of money on their purchase.
Ashton Mills. Wipe It Free: Secure Wiping Software. www.cso.com.au
Any company wants to have confirmation that its confidential data will not fall into the wrong hands, and a home user should not leave traces of personal information and transactions credit cards, because attackers can take advantage of them.
Before you transfer the computer to strangers, you should make sure that all data from it is deleted in compliance necessary measures security. In this case, simply deleting data or formatting a disk partition is not enough - the units and zeros that make up the information do not disappear anywhere, and they can be easily restored using specialized tools.
Naturally, demand creates supply, and therefore many tools have already been created for safely erasing information from disks. Moreover, to perform the relevant operations it is not at all necessary to purchase expensive software, which will undoubtedly please accountants and financiers. A lot of free tools have been developed that do for the user everything that he needs. However, as will be noted later, paid tools also find their customers.
Software designed for reliable information deletion is divided into two large classes based on processing of the file system or the disk itself. It is clear that in the second case the disk is erased, and in general, such a method would be preferable if guarantees are needed. Even when a program efficiently overwrites a file by overwriting it many times, a copy of this file or data can be saved in a page file, in syslog data, or in temporary files. However, it all depends on what level of security is needed.
This review will cover both very popular tools and programs that you probably never heard of. We hope that this will help you navigate the world of affordable tools and understand how they work.
The popular CCleaner tool designed to delete temporary files, clear browser cache, files system logs and other garbage, copes well with its tasks.
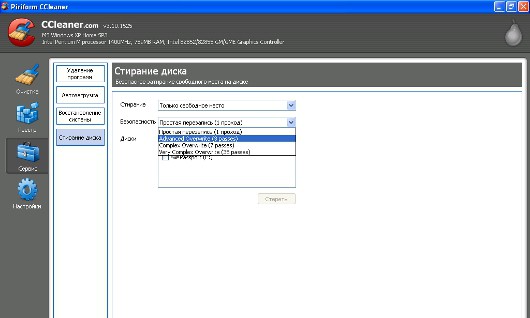
In addition, he has the Drive Wiper tool in the Tools section, which frees up space or the entire disk using four methods, from single-pass dubbing to the Gutman 35-pass algorithm. CCleaner is inferior in functionality to the other products included in this review, but it does its job quite well. In addition, it is distributed free of charge.
Slimware Slimcleaner Shredder
Slimcleaner is the actual Slimlean CCleaner equivalent with the Shredder tool.
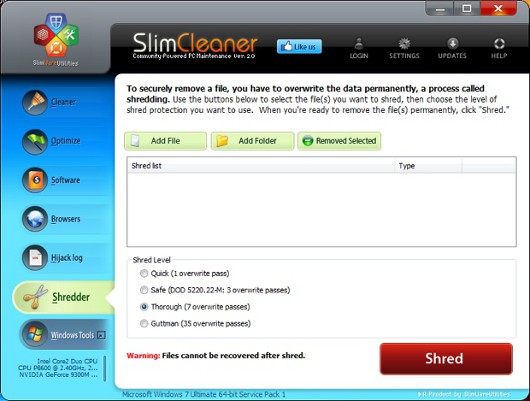
The user can choose the appropriate method of erasure, starting from a single-pass and ending with the Gutman 35-pass algorithm (see the section "Grades of safe removal"). Before pressing the Shred button, it is proposed to make a list of deleted items, which includes files and folders located in different places. Although there is no obvious way to erase everything from the disk, you can achieve the corresponding effect by selecting Folder and clicking on the root of the disk. However, this procedure is not equivalent to completely erasing the disk, since the file system structures are preserved in this case. A good product and again - free.
Darik "s Boot and Nuke
Darik's Boot and Nuke Utility Forms boot disk based on Linux, the sole purpose of which is to erase the entire drive to a state where even the most corrosive forensic examination will not produce any result.

It is also allowed to erase data from multiple disks at once. Their total number is limited only by the number of system interfaces and PCI bus bandwidth. It really can be very useful. Boot and Nuke erase methods range from a simple one-pass to a 35-pass Gutman algorithm. The program supports various standards (for example, the US Department of Defense “short” erase standard) and pseudo-random number generator (PRNG) streams generated using the Mersenne Whirlwind algorithm. This is not to say that everything was done very beautifully (after loading the disc, only ASCII text code will appear on the screen), but after all the procedures have been completed, the “enthusiasts” who retain the hope of recovering the destroyed information can only sympathize and wish good luck. The Linux-based Boot and Nuke boot disk is free.
Active @ KillDisk
The Active @ KillDisk utility, according to its developers, supports 17 different security standards (the “Gradations for Safe Removal” section explains why most of them are not needed), including the popular methods used by the military.

Unlike other tools, KillDisk comes in versions for Windows and for DOS. You can work with the first one directly in the operating system environment or from a boot disk. This allows you to erase data on the drive where Windows is located. This utility helps clean up free space. It contains a built-in disk viewer that helps you compare clusters before and after the procedure. In the free demo mode, only single pass dubbing is supported. All other methods require the purchase of the Pro version, which has an initial price of $ 50 for personal use and $ 1,500 for corporate use.
Disk wipe
The impressive compact utility Disk Wipe fully lives up to its expectations. It does not require installation and works in offlineby supporting seven methods. These include the Gutman 35-pass algorithm, technologies that meet the requirements of the British and Russian standards, as well as the US military standard. Like Active @ KillDisk, disk program Wipe has built-in disk viewers, and its volume does not exceed 1 MB.
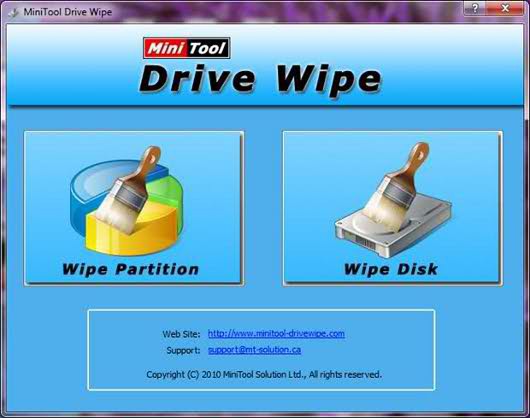
As an additional option, formatting the disk and writing to it a new file system are offered. There are no tools for working with individual files or folders here, but you should not expect such options from a utility called Disk Wipe.
Acronis Drive Cleanser
Acronis is known for its popular apps for reserve copyoriented both to corporate clients and home users. In addition, its product range includes Drive Cleanser, designed to safely remove information from disk.
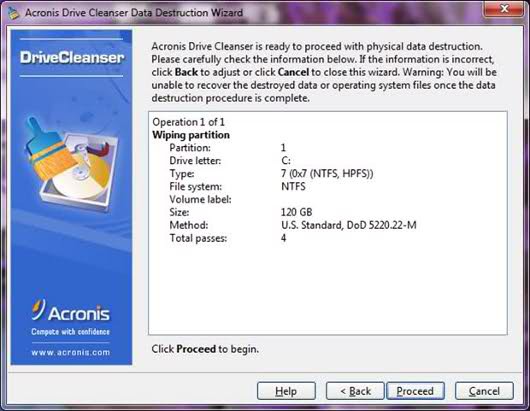
It is a little sad that during the installation process you will need an additional driver and you will have to reboot the system - and all this for a simple disk cleanup? In fairness, it should be noted that the utility is highly flexible, supporting not only the fast execution of standard algorithms and data deletion according to the Gutman method and the standard of the US Department of Defense, but also uses its own technology to erase information and determine the data written to the disk. In addition, you can create a boot disk with the means of reliable deletion of information placed on it (approximately the same thing was observed in the Darik application). Drive Cleanser software has a 15-day trial period. For the right to use the utility without restrictions on one computer, customers will have to pay $ 61.
East Tec Dispose Secure
Developed by East Tec's Dispose Secure software, like the other tools described here, you can create a boot disk. Its main advantage is the ability to manage information from networked computers from a single console.
All supported standard methods cleaning, as well as several new combinations, for example, the original method 3 + 7 + 3. In Network Sanitiser mode, data is deleted remotely from other machines with their MAC address or via network connection. This allows you to simultaneously access the disks of several machines at once, without leaving your workplace. The trial version clears only a quarter of the disk. A fully functional option that allows you to reliably remove from the disk all previously recorded data on it, can be purchased for $ 24.
Iolo drive scubber
Iolo Drive Scubber has a simple and nice interface. In most modes, a button is displayed on the screen that allows you to get additional informationthat serves as a good help for beginners. The utility runs both in Windows and from a previously created bootable media. Thanks to this, you can delete data from those drives on which it is deployed. operating system.
It supports simultaneous erasing of multiple disks at once and overwriting free space, not busy files. It is worth noting that this product belongs to the few that offer only one method that meets the DoD 5220.22-M standard. The user can independently set the number of passes and define their own patterns. In Desktop Incinerator mode, the utility acts as the Recycle Bin, supporting algorithms for the reliable destruction of deleted files. The trial version features are limited to three launches. A full-featured version with a license to use on three machines costs $ 50.
Clean disk security
Despite its big name, the Clean Disk Security utility cannot clean disks and erase individual files. It got into the review because it is close to CCleaner in functionality - cleaning the Recycle Bin, browser cache, browsing history, cookies, etc. are supported.
The user gets the opportunity to reliably destroy the data after they are deleted, which CCleaner can not do. Simple cleaning in several passes is supported, as well as two other modes, including data deletion using the Gutman method. Although the application cannot be used to clean the entire computer, it can come in handy for those who want to securely delete personal account information. Clean Disk Security belongs to the category of shareware software.
Jetico bcipe
BCWipe software is integrated directly into the Windows shell, which allows you to safely delete files and folders through the right-click context menu or through the Task Manager.
The tools built into the Task Manager provide scheduled deletion, cleaning free space and selected files and folders. A fairly wide range of methods is supported, including the popular military and Gutman algorithms. Additionally, you can clear the FAT and NTFS directories, as well as the space reserved by the system. The delivery includes a real-time paging file encryption mechanism. Fans Apple company Jetico offers a Mac version. The demo version can be downloaded from the developer's site. The full-featured version is priced at $ 50.
MiniTool Drive Wipe
The simplicity of the proposed tool should be emphasized here. The MiniTool Drive Wipe interface has only two buttons - Wipe Partition and Wipe Disk. After clicking on them, a dialog box with an image of the disk partition table is displayed. Depending on the selected mode, you can mark individual partitions on disks or entire disks.

Then you need to choose one of five methods (among others, the US Department of Defense standard with three and seven passes is supported), click the execute button and wait for the process to complete. The tool is supplied free of charge, it is intended solely for personal use. Its use for commercial purposes is prohibited.
Lavasoft file shredder
Lavasoft Utility File shredder, as its name implies, is designed to work with files and file system - The functions for cleaning disks and their partitions are not supported. But the set of operations with files and folders is very diverse. Three basic algorithms and 13 are offered by default. various methods, including popular military standards, and, of course, the Gutman algorithm.
The utility has assistants for cleaning files and folders, Recycle Bin, free disk space and system fileswhich include temporary files, browser cache, and cookies. Perhaps the functionality of File Shredder is not as wide as that of the other tools considered in our review, but the helpers noticeably simplify the work with this utility. The software has a trial period, after which you will have to pay $ 30 for a fully functional version.
Eraser
Like File Shredder, Eraser supports 13 algorithms that meet the requirements of various military standards, as well as a simple one-pass method for recording pseudorandom data (its usefulness is explained in the "Gradations of Safe Deletion" section).

Jobs related to deleting information can be run in advance certain time or after rebooting the system. Supports cleaning files, folders, Recycle Bin and free space. The interface is nothing special, but at the same time, Eraser has several unique features. When cleaning files and free space, it is acceptable to use two different methods. For example, free space can be processed by quick simple rewriting, and files can be destroyed by executing a slow multi-pass algorithm.
When erasing, locked files (as a rule, these are currently used or system files) can be automatically unlocked.
Of particular interest is the function that helps the user to hide his actions, replacing for disguise deleted files some other. Finally, the Eraser tool is not just free - it comes with open source.
Which utility is better?
The answer to this question is determined by your needs, and in order to get it, you need to do with each of the utilities all the operations that you might potentially need. Our subjective choices were awarded Gold, Silver and Bronze Prizes.
No special need to buy for money software for reliable data deletion, unless you need a commercial license or some specific functions (for example, the function of clearing information over the network, or encrypting the paging file. In general, all methods have already been tested, proved their worth and meet the requirements of the standards, which they are based.
Do not even torment your disk for four days with 35 passes of rewriting, achieving absolute reliability. The author himself, who proposed a comprehensive 35-pass algorithm, which is mainly used now, argued that overwriting with random data in one pass is quite enough for modern disks.
So we choose our programs to taste and go! Have a good work!
Safe Gradation Removal
Most programs designed to safely delete data support several different methods. They differ in the number of passes to overwrite a file or disk, the nature of the data used when overwriting, or a combination of these two parameters.
This method was first proposed by Peter Gutman and Colin Plum in 1996 to erase information recorded on magnetic tape in the MFM and RLL formats. Combinations of random data and data templates were selected specifically to exclude the possibility of restoring previously recorded information on the tape even using special equipment (which intercepts and analyzes analog signals and, by comparing them with digital, tries to recognize what was previously stored on the medium.
The Gutman and Plum method is often used without taking into account the specifications of modern discs. Users still prefer to perform all 35 passes, whereas even many years ago in most cases, according to the authors of the method themselves, only ten were enough. The number of passes was determined by the type of medium, and most of them were intended for certain coding mechanisms used when recording information on hard disks that time. With increasing recording density, the method ceased to be relevant.
In a study published in 2006 by the National Institute of Standards and Technology, one pass is enough to prevent data recovery on modern hard drives.
At the same time, there are a number of standards defined by government and military organizations around the world, in particular the Australian Radio Defense Authority and the US Department of Defense, which take data security seriously. For reliable erasure of information (apparently, in order to exclude accidents during the destruction of information), the US Department of Defense recommends three passes, and the Australian Radio Defense Authority advises to refuse to overwrite data altogether. From the point of view of safety, the demagnetization procedure is considered correct (for more details, see the section “Demagnetization”), and ideally, the physical destruction of the medium. Naturally, both of these methods are more effective, but they also have an obvious drawback - the hard drive becomes unusable after performing such operations.
Erase on Linux
As you would expect, erasing data in the Linux environment is done through free tools, and they are part of any popular Linux distribution.
There are several options, but the simplest of them are the two presented below.
Erasing a single file is done using the shred command, which, like the ones discussed here windows utilities, performs repeated rewriting of the data (the number of repetitions is set by the user) by randomly selected patterns (this includes a number of Gutman sequences). In addition, the file is renamed many times to remove information in the catalog tables, and zeros are written in its place. The shred command may look like this: shred –zvun10 / home / CSO / testfile. The file is deleted, overwritten ten times, and at the end its contents are replaced with zeros. Moreover, all information about the progress of the command is displayed on the screen. By the way, the Shred utility was written by Colin Plum.
Erasing the entire disk is done by the dd command, which has a very long history. This tool supports a variety of modes, ranging from mirroring disks to create snapshots of partitions to low-level reading. You can clear the disk by entering the command: dd if \u003d / dev / urandom of \u003d / dev / sda bs \u003d 1M. The if and of parameters determine the input and output files (in this case we are talking about the whole device), and bs is the block size. Specified command reads random data from the / dev / urandom file and writes it directly to disk until it is full. Another option is to use / dev / zero as the input file. And then the disk will be filled with zeros.
It must be remembered that the corresponding commands should not be entered in the Linux environment for the disk on which the system is recorded. You can boot from a Linux Live CD (for example, from the popular Ubuntu Live CD) and run the command in relation to the Windows drives connected to the computer.
Demagnetization
Of course, the use of software is not the only way to destroy information. To more reliably remove information from media with magnetic properties, it is worth using a magnet.
Moreover, it must be very powerful. During demagnetization, powerful magnets move around the device, creating moving magnetic fields that effectively destroy the data stored on the media. The advantage of demagnetization is that the effect is on the entire surface of the disk, including partition tables, boot sectors and low level formatting information. As a result, the disk is put into an inoperable state (since the low-level formatting data has been deleted), and it can only be restored by the manufacturer, but provided that the magnetic pulses did not damage the engine. Commercial demagnetization systems cost from 30 thousand to 140 thousand dollars.
The question remains, will it be possible to demagnetize the disk using a powerful magnet on its own? In most cases, the answer is yes. Magnets made of neodymium, rare earth metal, sold in electronic stores, create very powerful force fields, thousands of times greater than the weight of the magnets themselves. Applying them to a drive is very effective, but, like commercial demagnetization systems, they can render the drive unusable.
Testing methodology
Before each test, a formatted disk was installed on the PC, onto which sample files were copied. For programs that erase individual files and disks as a whole, sectors were marked where the files were located. The computer booted from the Linux Live CD, after which the hdparm command was entered with the --fibmap and --readsector options. This made it possible to find and read sectors of the drive in which the files were physically located.
Then the files or the disk were erased in the Windows environment, the computer was loaded from the Linux disk again, and the sectors were read again. Thus, it was possible to verify that those sectors in which the files were located no longer contain the previous data, or rather, include random or zeroed information.
The duration of the erasing procedure was not measured, since all products are performed at a good level and their performance is limited only by the speed of the input / output subsystem.
Solid State Drive Features
In the past few years, solid state drives (SSDs) are gaining increasing popularity among both corporate and home users. They work quickly, quietly and consume less electricity, however, their inherent design features affect their safety. Unlike traditional spinning plates, NVRAM memory, on the basis of which solid-state drives are built, can withstand a limited number of write cycles. In practice, the service life of SSDs still remains quite decent - long-term studies that accurately calculate the number of recording cycles during the service period have not yet been carried out. In addition, manufacturers use special firmware to extend their life. This technology, called wear leveling, is to evenly distribute recording cycles between all memory cells.
In practice, this means that when overwriting a file using the operating system, the new file is saved in a different place. And even if you “delete” the file from the disk, recovering it will not be difficult. Secure file deletion and free space deletion are not applicable to SSDs for the same reason. The transferred sectors that the operating system sees are not related to the initial physical placement of data in the NAND chip.
Unfortunately, with increased security requirements, this task actually has no solution. The only way is connected with the so-called safe erase mode. All SSD manufacturers support this feature. It consists in restoring the factory state of the device (unless, of course, taking into account the degree of wear and tear) and writing zeros to all cells. In this case, you get everything or nothing, since selective safe erasing of files, folders or partitions, unlike disks with rotating plates by solid-state disks, is not supported.
In addition to the fact that SSDs are notable for the complexity of recording algorithms, many of them have a special memory area, the dimensions of which sometimes reach several gigabytes. It is used by garbage collection procedures or procedures for allocating new sectors in the event of failure of individual cells. This area also contains old data that can be recovered with the necessary tools.
Contrary to popular belief, in fact, the contents of the memory cells are not erased by the TRIM command, and a special flag is set in the cluster drive circuit. It indicates that the cells do not need to perform the full cycle of read / modify / write operations that are usually initiated when information is written to the cell that already contains data. Until these cells are written new information, they will store old data.
Based on all of the above, we can conclude that if security is more important to you than speed, then using solid-state drives will not be the best solution.