Want to allow users with a standard account to run applications with administrator privileges without UAC or a password request? Then I will tell you how to do it. We will create a shortcut using the command runas / savecredwhich saves the password. I note that this can be considered a security hole - an ordinary user will be able to use runas / savecred to execute any command on behalf of the administrator without entering a password. However, in some situations this can be useful - for example, if you want your child from under a standard account to be able to run applications as an administrator without asking you.
Enable admin account
First of all, you need to enable the built-in administrator account, which is disabled by default. So, right-click on the command line shortcut and select "Run as administrator".
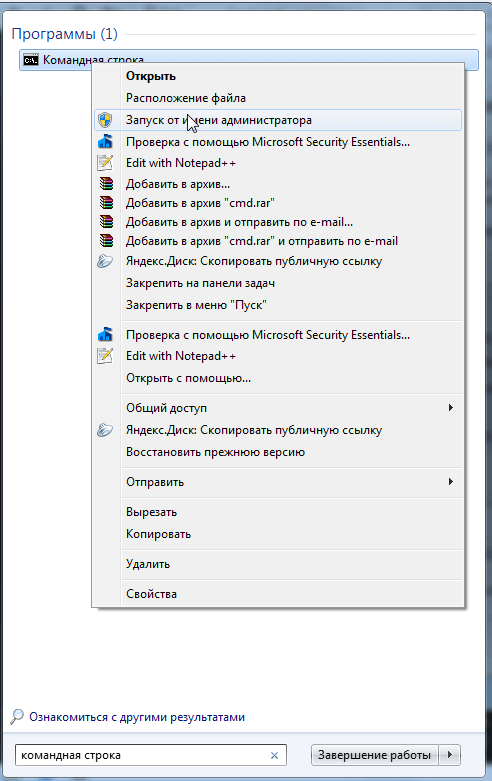
In the command prompt window that opens, run the following command:
net user administrator / active: yes
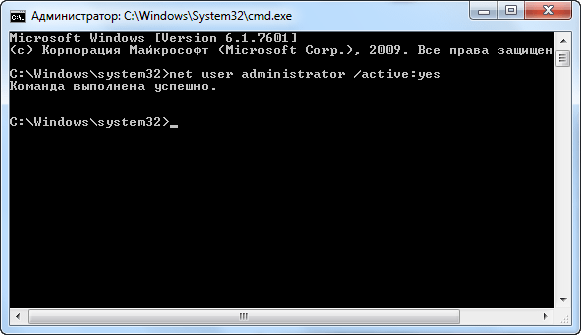
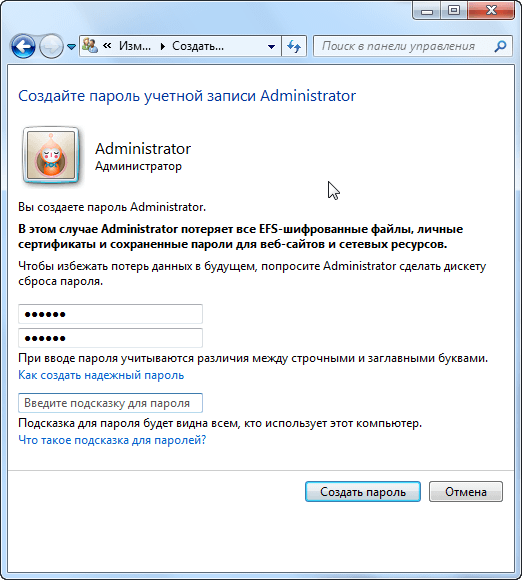
The account is now enabled, although without a password. To set a password, open the Control Panel, select the User Accounts and Family Security category, and then open the User Accounts menu. Next, click on the link “Manage another account”.

Select an administrator account, click on the "Create Password" button, and create a password for the administrator account.
Create a shortcut
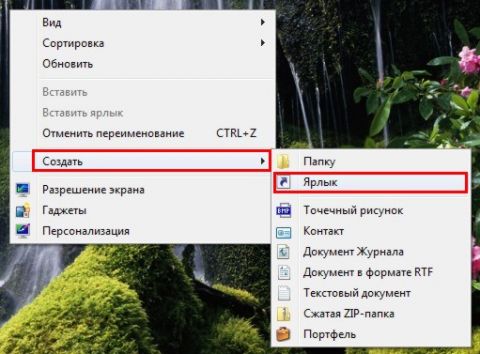
Now we will create a shortcut that will launch the application with administrator privileges. Right-click on the desktop, select "Create", and then click on "Shortcut".

In the window that opens, enter the command of the following type:
runas / user: Computername\\ Administrator / savecred “ C: \\ Path \\ To \\ Program.exe“
Please note that you need to replace Computername in the name of your computer, and C: \\ Path \\ To \\ Program.exe to the full path to the program you want to run. For example, if the computer name is Laptop, and the program you want to run is Auslogics BoostSpeed, you need to enter the following path:
runas / user: Laptop \\ Administrator / savecred “C: \\ Program Files \\ Auslogics \\ Auslogics BoostSpeed \u200b\u200b\\ BoostSpeed.exe"
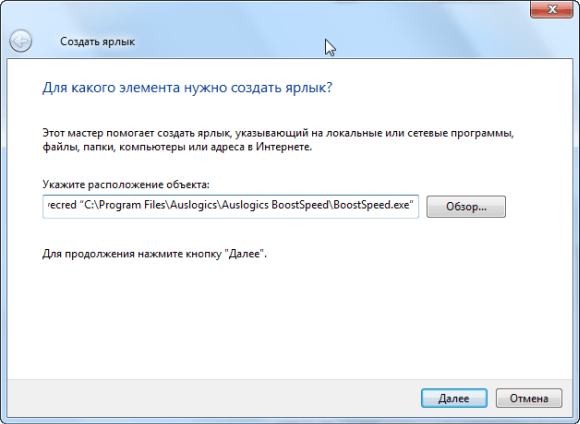
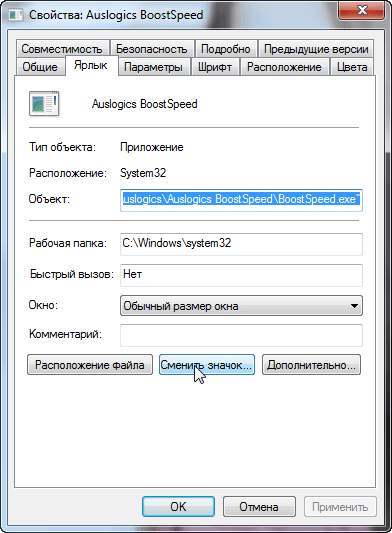
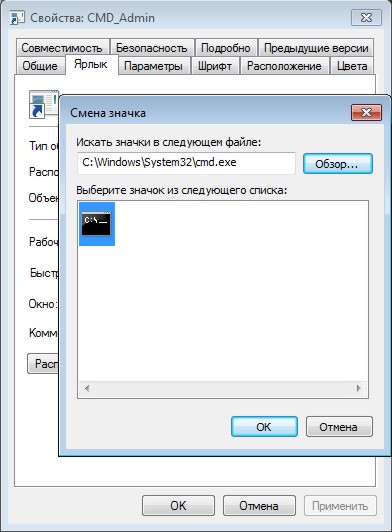
In the next window, enter a name for the shortcut. If desired, you can select an icon for a new shortcut - right-click on it and select "Properties".

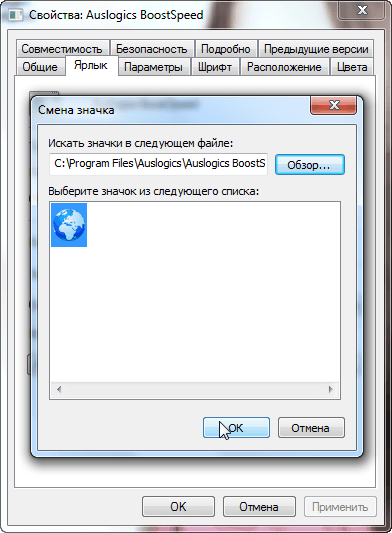
In the "Properties" dialog box, click on the "Change Icon" button and select the appropriate one.
When you double-click the shortcut for the first time, you will be asked to enter the password for the administrator account that you created earlier.
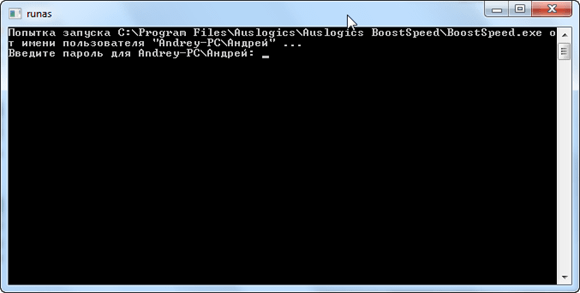
This password will be saved - the next time you run the program, you no longer have to enter it again.
As mentioned above, under standard accounts, users can run any program with administrator rights without entering a password (using the runas / savecred command), so keep that in mind.
The administrator password is stored in the "Credential Manager" - if you want to delete the saved password, you can do it from there.
Have a great day!
Some Windows applications require elevated permissions, and you need to run them as administrator. The query " User Account Control"(User Account Control or Uac), in which the system asks for your consent to launch the application.
Many users incorrectly believe that "User Account Control" only interferes and disable it. At the same time, computer security is seriously affected. user consent to launch applications is no longer required, and any malicious program can run and run unhindered. The presence of an antivirus also cannot 100% guarantee computer security.
In this article I will tell you how to simplify the process of launching selected applications on behalf of the administrator without disabling UAC (in whole or in part) and without compromising security.
To run the application as administrator, you can use several methods:
As an example, we will run command line (cmd) as administrator.
Method No. 1 (normal) - start via the right mouse button (UAC request is displayed)
Right click on the icon desired application and select " Run as administrator":

Method number 2 - start using " Ctrl + Shift + Enter"(UAC request is displayed)
Click Start, in the search bar, type the desired command and click Ctrl + Shift + Enter.
Method No. 3 - set the launch as administrator in the shortcut properties (UAC request is displayed)
Right-click on the desired shortcut and select " The properties".
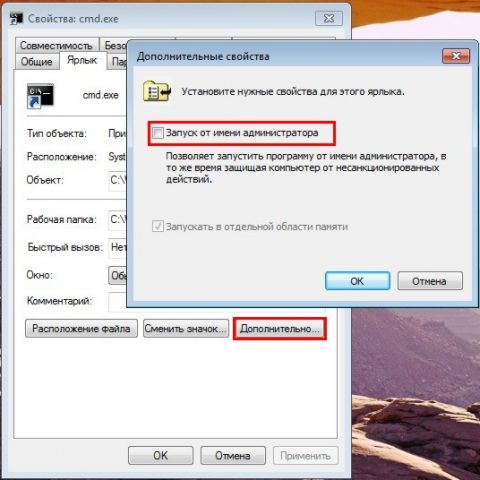
Go to the " Label"click" Additionally"check the box" Run as administrator":
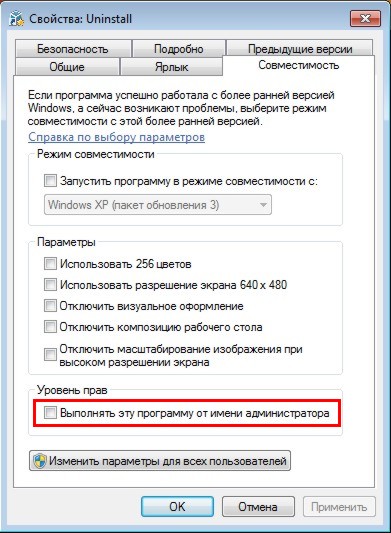
Or go to the " Compatibility"and check the box" Run this program as administrator":
Method number 4 - simplify the launch for selected applications using the task scheduler (UAC request is not displayed)
Important! This method only works for accounts in the group. Administrators. At ordinary users it will not work, because their rights are limited to the ceiling.
We pass to the most interesting way. If there is an application that you constantly run, and it is received from a reliable software manufacturer, for example, this windows application - You can simplify the launch. Create a shortcut for desired program does not take more than 2 minutes and this will get rid of unnecessary actions in the future. We launch task Scheduler (Start---> All programs ---> Standard---> Office---> Task Scheduler) and click " Create task":
Indicate Namefor a new task and check the box " Perform with the highest rights":
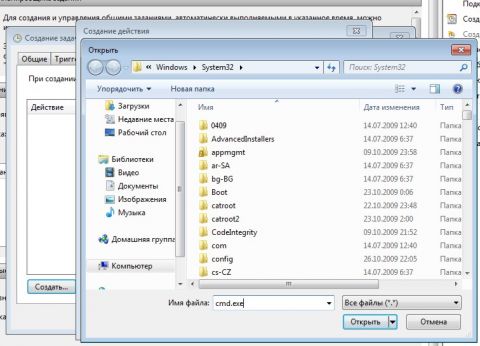
Go to the tab Actionsclick " Create", in the next window click" Overview":

Specify the path to the desired application and click " Open":
Enlarge picture
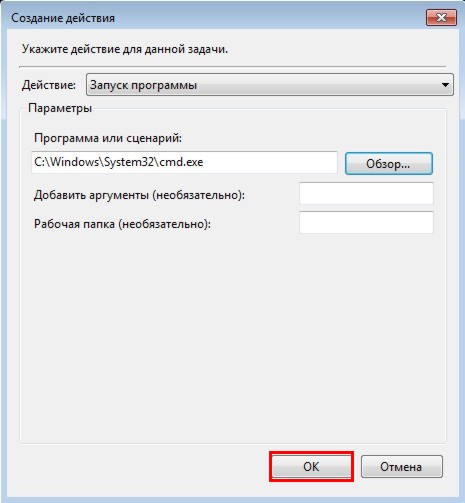
Push " OK":
Close the scheduler and move on to creating a shortcut.
To create a shortcut on the desktop, right-click, select " Create" ---> "Label":
In field Property location enter:
Schtasks / run / tn cmd_admin
where cmd_admin - name of the task we created. If the name contains spaces, it must be enclosed in quotation marks.
Set the label name:

Enlarge picture
Shortcut created and ready to use.
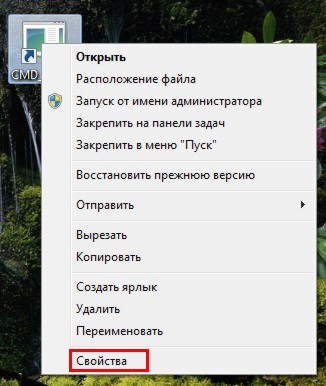
To change the icon - right-click on the shortcut, select " The properties":
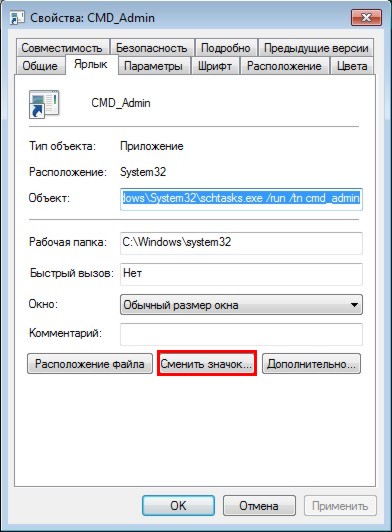
Go to the " Label"and press " Change icon":
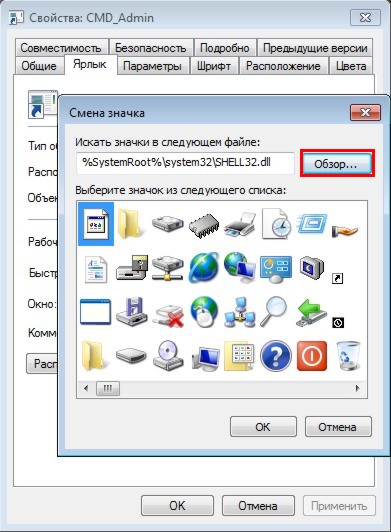
"Overview..."
Specify the path to the program:
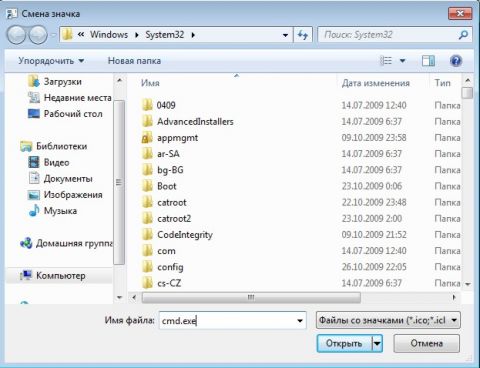
Enlarge picture
Select the desired icon and close both windows with the " OK":

Now, launching the desired application as an administrator is performed by double-clicking on the created shortcut, while the UAC request is not displayed and the security remains intact.
Utility for automation of "Method No. 4"
In case you need to create shortcuts for a large number of programs, it is convenient to use the utility.
Working with the utility comes down to two simple steps:
- Installation
- Drag and drop the executable file (* .exe, * .bat, * .cmd) onto the utility shortcut:

Auto focus on a running program
The specifics of launching applications from the scheduler is that the focus on the window is not translated and, for example, to type a command on the command line, you have to click on the window additionally. Such behavior can help in automating routine scheduled operations, but for "Method No. 4" this is not always convenient.
There are several methods to work around. They work a little differently, so choose the most suitable one. The first is more convenient for running programs, and the second for running scripts.
Add when creating the task:
Using the start command
Program or script:
Arguments:
/ c start / d "program_path" file_name.exe
/ c start / d "C: \\ Windows \\ System32 \\" cmd.exe
Using NirCmd Utility
Program or script:
Path_k_nircmd \\ nircmd.exe
Arguments:
Exec show "program_path \\ file_name.exe"
Exec show "C: \\ Windows \\ System32 \\ cmd.exe"
Launching the Run dialog as administrator
Similar to launching the command line, you can configure the launch of the " Run", and the commands entered into it will also be launched on behalf of the administrator. The convenience of this approach is that the list of previously used commands is saved, and you can select the desired one from the list.
When creating a task in the scheduler, in the " Action creation"indicate:
in field " Program or script":
Rundll32
in field " Add arguments":
Shell32.dll, # 61
Download the utility, unpack it. We launch the command line, enter the desired command, the syntax is quite simple:
<путь к утилите> <путь к нужному приложению>
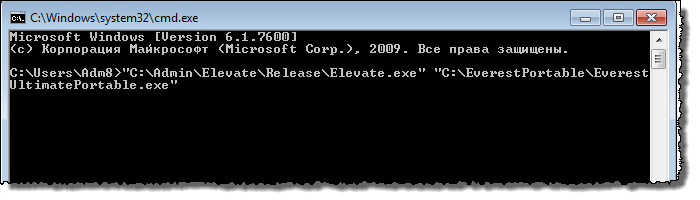
A UAC prompt is displayed and the application starts as administrator.
Note: In context windows menu 7 there is a very convenient function to copy the file path: hold Shift, right-click on the file, select " Copy as path".
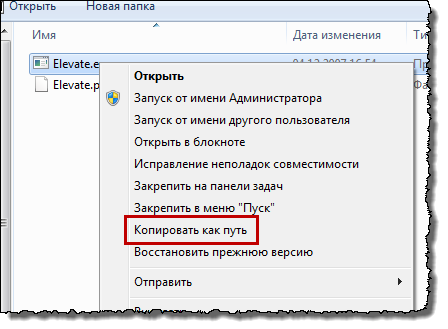
Running programs by a user as administrator without entering an administrator password
Important! This method is unsafe because it allows a user with limited rights to run code with full rights. A cunning user or malware can take advantage of this and compromise the system.
Consider another interesting problem: your account windows record belongs to the group of administrators, there is one or several accountsincluded in the user group. The user needs to run a program that requires elevation of privileges. Usually it looks like this: the user right-clicks on the file and selects "Run as Administrator", and a request for entering the administrator password is displayed:

Of course, giving out an administrator password to users is not a good idea. To get around this, we will use the AdmiLink utility of Alexei Kuryakin. With it, the administrator can create a shortcut for the user to launch the necessary program, while entering the administrator password is required only 1 time - when creating the shortcut. When the user starts the program, the password will be transmitted in encrypted form.
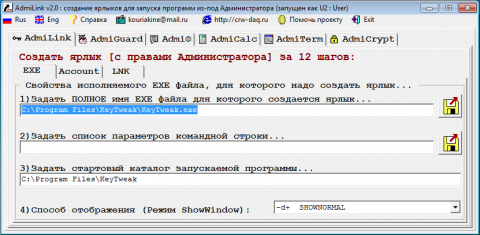
This method will work if starting the program is possible only on behalf of the administrator and the developer did not forget to indicate this condition in the manifest. However, it remains a large number of old programs or programs that can be started as in normal mode, and on behalf of the administrator (in this case, a different set of functions will be available). When you try to run such a program using AdmiLink, it starts in normal mode (without administrative privileges). And if you try to put a checkmark in "Method number 3. The original style of the author is saved.
What if you need to run the program, but you do not want to install it? Zero Install to the rescue!
Billions of people around the world use computers or laptops on the operating room. windows system. Usually, we install programs, after which they take free place on disk and use random access memory. This reduces the speed of the computer.
Today we will tell you how you can increase computer performance and reduce the load on memory. To do this, you need to run the necessary programs without installing them.
How to run the program without installation?
1. Download Zero Install.
First, download the Zero Install software, which allows you to run programs without having to install them on your computer.
2. Install Zero Install.
Once you have downloaded Zero Install, double-click on the file to install it. Then run new program on your computer.

3. Click onmasonry "Catalog".
As soon as Zero Install is launched on the computer or windows laptop, you should go to the “Catalog” tab. Click on the “Refresh list” button to update the list of available programs.
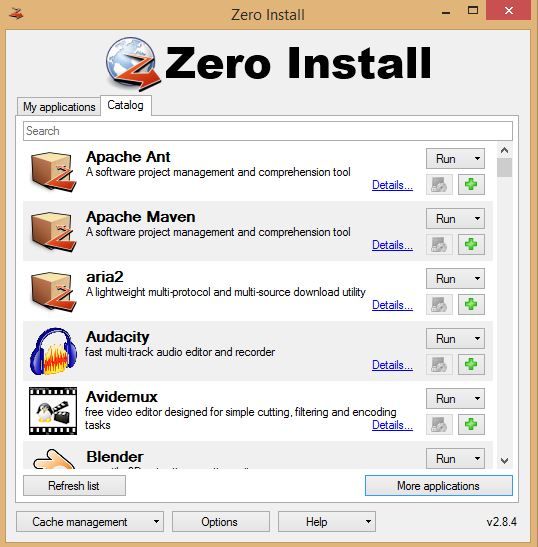
4. Select a program to run.
Look carefully full list available programs. If you find the program you need, select it and click “Run”. Some programs may choose firefox browser or Mozilla to run. Just wait for the full download. software, after which you can run it on your computer without installing it.
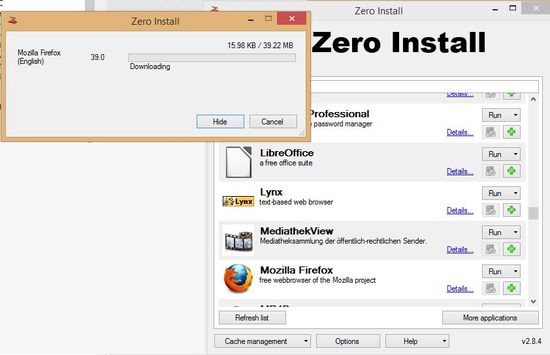
Summarizing
If your computer does not have enough free memory or power to run the program, you can use Zero Install. I think this is a great way not to litter your computer with the programs you need at one time.
Also, your computer may not have enough power to run certain programs, for example, Eclipse IDE, JetBrains, NetBeans, etc. These are really hard programs for developers who consume a large amount of RAM.
Zero Install will help launch these, and many other programs, without installing them on a computer.
The most important thing was not described in sufficient detail: how to run this code on real hardware? How to create your own boot disk? In this article, we will answer all these questions in detail (partially, these issues were discussed in the previous article, but for the convenience of reading we allow ourselves a little duplication of material).
On the Internet there are a lot of descriptions and tutorials on how to write your own mini-OS, even there are hundreds of ready-made little hobby-OS. One of the most worthy resources on this subject, which I would like to highlight, is the osdev.org portal. To complement the previous article about PCI (and the ability to write subsequent articles about the various functions that are present in any modern OS), we will describe step by step instructions to create a boot disk with the usual program in C. We tried to write as detailed as possible so that we could figure it out on our own.
So, the goal: having spent as little effort as possible, create your own bootable USB flash drive, which just prints the classic “Hello World” on a computer screen.
To be more precise, we need to "get" into protected mode with disabled page addressing and interrupts - the simplest processor mode with the usual behavior for a simple console program. The most reasonable way to achieve this goal is to build a kernel that supports the multiboot format and load it using the popular boot loader grub. An alternative to this solution is to write your own volume boot record (VBR), which would load your own written loader (loader). A decent bootloader, at least, should be able to work with the disk, with the file system, and parse elf images. This means that you need to write a lot of assembler code, and a lot of C code. In short, it’s easier to use Grub, which already knows how to do everything necessary.
To begin with, a certain set of compilers and utilities is required for further actions. The easiest way is to use some kind of Linux (for example, Ubuntu), since it will already contain everything you need to create a bootable flash drive. If you are used to working in Windows, you can configure a virtual machine with Linux (using Virtual Box or VMware Workstation).
If you use Linux Ubuntu, then first of all you need to install several utilities:
1. Grub. To do this, use the command:
Sudo apt-get install grub
2. Qemu. It is needed to quickly test and debug everything (Link to the article about the debugger), for this the command is similar:
Sudo apt-get install qemu
Now our plan looks like this:
1. Create a C program that prints a line on the screen.
2. compile from it an image (kernel.bin) in miniboot format so that it is available for download using GRUB.
3. Create a boot disk image file and format it.
4. Install Grub on this image.
5. copy the created program (kernel.bin) to the disk.
6. burn the image to physical media or run it in qemu.
and the system boot process:
To make it work, you will need to create several files and directories:
Step 1. Creating the code of the target program (kernel):
Create a kernel.c file that will contain the following code that prints a message on the screen:
#include "printf.h" #include "screen.h" #include "types.h" void main (void) (clear_screen (); printf ("n \u003e\u003e\u003e Hello World! n");)
Everything is familiar and simple here. Adding the printf and clear_screen functions will be discussed later. In the meantime, you need to supplement this code with everything necessary so that it can be loaded by Grub’s.
In order for the kernel to be in multiboot format, you need the following structure in the first 8 kilobytes of the kernel image:
If all these conditions are met, then Grub passes through the% eax and% ebx registers a pointer to the multiboot Information structure and the value 0x1BADB002, respectively. The multiboot Information structure contains various information, including a list of loaded modules and their location, which may be necessary for further loading of the system.
In order for the program file to contain the necessary signatures, create a loader.s file with the following contents:
Text .global loader # making entry point visible to linker # setting up the Multiboot header - see GRUB docs for details .set FLAGS, 0x0 # this is the Multiboot "flag" field .set MAGIC, 0x1BADB002 # "magic number" lets bootloader find the header .set CHECKSUM, - (MAGIC + FLAGS) # checksum required .align 4 .long MAGIC .long FLAGS .long CHECKSUM # reserve initial kernel stack space .set STACKSIZE, 0x4000 # that is, 16k. .lcomm stack, STACKSIZE # reserve 16k stack .comm mbd, 4 # we will use this in kmain .comm magic, 4 # we will use this in kmain loader: movl $ (stack + STACKSIZE),% esp # set up the stack movl% eax, magic # Multiboot magic number movl% ebx, mbd # Multiboot data structure call main # call C code cli hang: hlt # halt machine should kernel return jmp hang
Consider the code in more detail. This code is almost unchanged from wiki.osdev.org/Bare_Bones. Since gcc is used for compilation, the GAS syntax is used. Let's take a closer look at what this code does.
All subsequent code will fall into the executable section .text.
Global loader
We declare the loader symbol visible to the linker. This is required since the linker will use the loader as an entry point.
Set FLAGS, 0x0 # assign FLAGS \u003d 0x0 .set MAGIC, 0x1BADB002 # assign MAGIC \u003d 0x1BADB002 .set CHECKSUM, - (MAGIC + FLAGS) # assign CHECKSUM \u003d - (MAGIC + FLAGS) .align 4 # align the subsequent data by 4 bytes. long MAGIC # place current value MAGIC .long FLAGS # place current value FLAGS. long CHECKSUM # place current value CHECKSUM
This code forms a signature of the Multiboot format. The .set directive sets the character value to the expression to the right of the comma. The .align 4 directive aligns subsequent contents to 4 bytes. The.long directive stores the value in four subsequent bytes.
Set STACKSIZE, 0x4000 # assign STACKSIZE \u003d 0x4000 .lcomm stack, STACKSIZE # reserve STACKSIZE bytes. stack refers to the range.comm mbd, 4 # reserve 4 bytes for the mdb variable in the COMMON area .comm magic, 4 # reserve 4 bytes for the magic variable in the COMMON area
During the boot process, grub does not configure the stack, and the first thing the kernel should do is configure the stack, for this we reserve 0x4000 (16Kb) bytes. The.lcomm directive reserves in the.bss section the number of bytes specified after the decimal point. The name stack will only be visible in the compiled file. The .comm directive does the same as .lcomm, but the symbol name will be declared globally. This means that by writing the following line in C code, we can use it.
extern int magic
And now the last part:
Loader: movl $ (stack + STACKSIZE),% esp # initialize stack movl% eax, magic # write% eax to magic address movl% ebx, mbd # write% ebx to mbd call main # call main cli function # disconnect interrupt from hardware hang: hlt # stop processor until interruption occurs jmp hang # jump to hang label
The first instruction saves the value of the top of the stack in the% esp register. As the stack grows down, the address of the end of the range allocated for the stack is written in% esp. The two subsequent instructions store in the previously reserved ranges of 4 bytes the values \u200b\u200bthat Grub passes in the% eax,% ebx registers. Then the main function, which is already written in C, is called. If you return from this procedure, the processor will loop.
Step 2. Preparation of additional code for the program (system library):
Since the entire program is written from scratch, the printf function must be written from scratch. To do this, prepare several files.
Create a common and include folder:
Mkdir common mkdir include
Create a commonprintf.c file that will contain the implementation of the familiar printf function. This entire file can be taken from the www.bitvisor.org/ project. The path to the file in the sources of bitvisor: core / printf.c. In the printf.c file copied from bitvisor, for use in the target program, you need to replace the lines:
#include "initfunc.h" #include "printf.h" #include "putchar.h" #include "spinlock.h"
per line:
#include "types.h" #include "stdarg.h" #include "screen.h"
Then, remove the printf_init_global function and all its references in this file:
Static void printf_init_global (void) (spinlock_init (& printf_lock);) INITFUNC ("global0", printf_init_global);
Then delete the printf_lock variable and all its references in this file:
Static spinlock_t printf_lock; ... spinlock_lock (& \u200b\u200bprintf_lock); ... spinlock_unlock (& \u200b\u200bprintf_lock);
The printf function uses the putchar function, which also needs to be written. To do this, create a commonscreen.c file with the following contents:
#include "types.h" #define GREEN 0x2 #define MAX_COL 80 // Maximum number of columns #define MAX_ROW 25 // Maximum number of rows #define VRAM_SIZE (MAX_COL * MAX_ROW) // Size of screen, in short "s # define DEF_VRAM_BASE 0xb8000 // Default base for video memory static unsigned char curr_col \u003d 0; static unsigned char curr_row \u003d 0; // Write character at current screen location #define PUT (c) (((unsigned short *) (DEF_VRAM_BASE)) [ (curr_row * MAX_COL) + curr_col] \u003d (GREEN<< 8) | (c)) // Place a character on next screen position static void cons_putc(int c) { switch (c) { case "t": do { cons_putc(" "); } while ((curr_col % 8) != 0); break; case "r": curr_col = 0; break; case "n": curr_row += 1; if (curr_row >\u003d MAX_ROW) (curr_row \u003d 0;) break; case "b": if (curr_col\u003e 0) (curr_col - \u003d 1; PUT ("");) break; default: PUT (c); curr_col + \u003d 1; if (curr_col\u003e \u003d MAX_COL) (curr_col \u003d 0; curr_row + \u003d 1; if (curr_row\u003e \u003d MAX_ROW) (curr_row \u003d 0;))); ) void putchar (int c) (if (c \u003d\u003d "n") cons_putc ("r"); cons_putc (c);) void clear_screen (void) (curr_col \u003d 0; curr_row \u003d 0; int i; for (i \u003d 0; i< VRAM_SIZE; i++) cons_putc(" "); curr_col = 0; curr_row = 0; }
The specified code contains simple logic for printing characters on the screen in text mode. In this mode, two bytes are used to write a character (one with the character code, the other with its attributes), written directly to the video memory displayed immediately on the screen and starting with address 0xB8000. The screen resolution is 80x25 characters. The character is directly printed using the PUT macro.
Now only a few header files are missing:
1. The file includescreen.h. Declares a putchar function, which is used in the printf function. File contents:
#ifndef _SCREEN_H #define _SCREEN_H void clear_screen (void); void putchar (int c); #endif
2. The file includeprintf.h. Declares the printf function, which is used in main. File contents:
#ifndef _PRINTF_H #define _PRINTF_H int printf (const char * format, ...); #endif
3. The file includestdarg.h. Declares functions to iterate over arguments whose number is not known in advance. The entire file is taken from the www.bitvisor.org/ project. The path to the file in the bitvisor project code: includecorestdarg.h.
4. The file includetypes.h. Declares NULL and size_t. File contents:
#ifndef _TYPES_H #define _TYPES_H #define NULL 0 typedef unsigned int size_t; #endif
Thus, the include and common folders contain the minimum system library code that any program needs.
Step 3. Creating a script for the linker:
We create the linker.ld file, which will be used by the linker to generate the target program file (kernel.bin). The file should contain the following:
ENTRY (loader) LMA \u003d 0x00100000; SECTIONS (. \u003d LMA; .multiboot ALIGN (0x1000): (loader.o (.text)) .text ALIGN (0x1000): (* (. Text)) .rodata ALIGN (0x1000): (* (. Rodata *) ) .data ALIGN (0x1000): (* (. data)) .bss: (* (COMMON) * (. bss)) / DISCARD /: (* (. comment)))
The built-in function ENTRY () allows you to set the entry point for our kernel. It is at this address that grub will pass control after the kernel boots. Using this script, the linker will create a binary file in ELF format. An ELF file consists of a set of segments and sections. The list of segments is contained in the Program header table, the list of sections in the Section header table. The linker operates with sections, the image loader (in our case, GRUB) with segments.
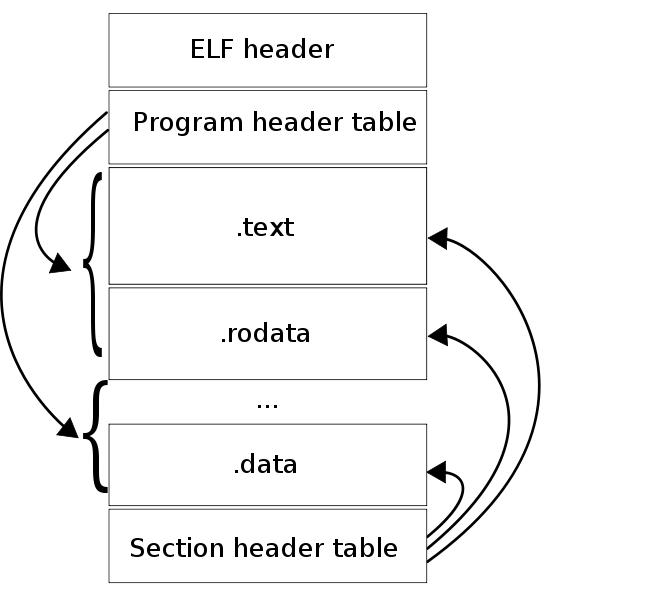
As you can see in the figure, the segments consist of sections. One of the fields describing the section is the virtual address at which the section should be at the time of execution. In fact, a segment has 2 fields that describe its location: the virtual address of the segment and the physical address of the segment. The virtual address of the segment is the virtual address of the first byte of the segment at the time the code is executed, the physical address of the segment is the physical address at which the segment should be loaded. For applications, these addresses always match. Grub downloads image segments at their physical address. Since Grub does not configure page addressing, the virtual address of the segment must match its physical address, since in our program virtual memory is also not configured.
LMA
This expression indicates to the linker that all subsequent sections are after the LMA address.
ALIGN (0x1000)
The directive above means that the section is aligned to 0x1000 bytes.
Multiboot ALIGN (0x1000): (loader.o (.text))
A separate multiboot section, which includes the .text section from the loader.o file, is designed to guarantee that the signature of the multiboot format gets into the first 8kb of the kernel image.
Bss: (* (COMMON) * (. Bss))
* (COMMON) is the area in which memory is reserved by the instructions .com and.lcomm. We place it in the .bss section.
/ DISCARD /: (* (. Comment))
All sections marked DISCARD are removed from the image. In this case, we delete the section .comment, which contains information about the version of the linker.
Now compile the code into a binary file with the following commands:
As -o loader.o loader.s gcc -Iinclude -Wall -fno-builtin -nostdinc -nostdlib -o kernel.o -c kernel.c gcc -Iinclude -Wall -fno-builtin -nostdinc -nostdlib -o printf.o -c common / printf.c gcc -Iinclude -Wall -fno-builtin -nostdinc -nostdlib -o screen.o -c common / screen.c ld -T linker.ld -o kernel.bin kernel.o screen.o printf .o loader.o
Using objdump’s, let's see what the kernel image looks like after linking:
Objdump -ph ./kernel.bin
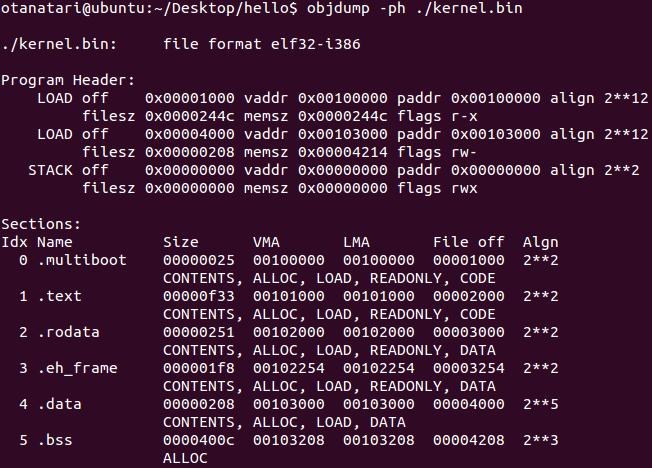
As you can see, the sections in the image coincide with those that we described in the linker script. The linker formed 3 segments from the described sections. The first segment includes sections.multiboot, .text, .rodata and has a virtual and physical address 0x00100000. The second segment contains the sections .data and .bss and is located at 0x00104000. So everything is ready to download this file using Grub.
Step 4. Preparing the Grub bootloader:
Create grub folder:
Mkdir grub
Copy several Grub files to this folder that are necessary for installing it on the image (the following files exist if Grub is installed on the system). To do this, run the following commands:
Cp / usr / lib / grub / i386-pc / stage1 ./grub/ cp / usr / lib / grub / i386-pc / stage2 ./grub/ cp / usr / lib / grub / i386-pc / fat_stage1_5 ./grub /
Create a grub / menu.lst file with the following contents:
Timeout 3 default 0 title mini_os root (hd0,0) kernel /kernel.bin
Step 5. Automate and create a boot image:
To automate the build process, we will use the make utility. To do this, create a makefile that will be going to compile source, build the kernel and create a boot image. The makefile should have the following contents:
CC \u003d gcc CFLAGS \u003d -Wall -fno-builtin -nostdinc -nostdlib LD \u003d ld OBJFILES \u003d loader.o common / printf.o common / screen.o kernel.o image: @echo "Creating hdd.img ..." @ dd if \u003d / dev / zero of \u003d. / hdd.img bs \u003d 512 count \u003d 16065 1\u003e / dev / null 2\u003e & 1 @echo "Creating bootable first FAT32 partition ..." @losetup / dev / loop1 ./hdd .img @ (echo c; echo u; echo n; echo p; echo 1; echo; echo; echo a; echo 1; echo t; echo c; echo w;) | fdisk / dev / loop1 1\u003e / dev / null 2\u003e & 1 || true @echo "Mounting partition to / dev / loop2 ..." @losetup / dev / loop2 ./hdd.img --offset `echo` fdisk -lu / dev / loop1 | sed -n 10p | awk "(print $$ 3)" `* 512 | bc` --sizelimit `echo` fdisk -lu / dev / loop1 | sed -n 10p | awk "(print $$ 4)" `* 512 | bc` @losetup -d / dev / loop1 @echo "Format partition ..." @mkdosfs / dev / loop2 @echo "Copy kernel and grub files on partition ..." @mkdir -p tempdir @mount / dev / loop2 tempdir @mkdir tempdir / boot @cp -r grub tempdir / boot / @cp kernel.bin tempdir / @sleep 1 @umount / dev / loop2 @rm -r tempdir @losetup -d / dev / loop2 @echo "Installing GRUB. .. "@echo" device (hd0) hdd.img n root (hd0,0) n setup (hd0) n quitn "| grub --batch 1\u003e / dev / null @echo "Done!" all: kernel.bin rebuild: clean all .s.o: as -o [email protected] $< .c.o: $(CC) -Iinclude $(CFLAGS) -o [email protected] -c $< kernel.bin: $(OBJFILES) $(LD) -T linker.ld -o [email protected] $ ^ clean: rm -f $ (OBJFILES) hdd.img kernel.bin
Two main goals are declared in the file: all - compiles the kernel, and image - which creates the boot disk. The all target, like the usual makefile, contains subgoals.s.o and.c.o that compile * .s and * .c files into object files (* .o), as well as a target for generating kernel.bin, which calls the linker with the script created earlier. These goals perform exactly the same commands that are listed in step 3.
Of greatest interest here is the creation of boot image hdd.img (target image). Let us consider in stages how this happens.
Dd if \u003d / dev / zero of \u003d. / Hdd.img bs \u003d 512 count \u003d 16065 1\u003e / dev / null 2\u003e & 1
This command creates an image with which further work will take place. The number of sectors was not chosen randomly: 16065 \u003d 255 * 63. By default, fdsik works with the disk as if it had CHS geometry in which Headers (H) \u003d 255, Sectors (S) \u003d 63, and Cylinders © depends on the size of the disk . Thus, the minimum disk size the fdsik utility can work with without changing the default geometry is 512 * 255 * 63 * 1 \u003d 8225280 bytes, where 512 is the sector size and 1 is the number of cylinders.
Next, a partition table is created:
Losetup / dev / loop1 ./hdd.img (echo c; echo u; echo n; echo p; echo 1; echo; echo; echo a; echo 1; echo t; echo c; echo w;) | fdisk / dev / loop1 1\u003e / dev / null 2\u003e & 1 || true
The first command mounts the hdd.img file to the block device / dev / loop1, allowing you to work with the file as a device. The second command creates the partition table on the device / dev / loop1, in which there is 1 primary boot partition a disk that spans the entire disk with the FAT32 file system label.
Then we format the created section. To do this, mount it as a block device and perform formatting.
Losetup / dev / loop2 ./hdd.img --offset `echo` fdisk -lu / dev / loop1 | sed -n 10p | awk "(print $$ 3)" `* 512 | bc` --sizelimit `echo` fdisk -lu / dev / loop1 | sed -n 10p | awk "(print $$ 4)" `* 512 | bc` losetup -d / dev / loop1
The first command mounts the previously created partition to the device / dev / loop2. The –offset option specifies the address of the beginning of the section, and –sizelimit the address of the end of the section. Both parameters are obtained using the fdisk command.
Mkdosfs / dev / loop2
The mkdosfs utility formats a partition in file system FAT32.
For direct assembly of the kernel, the previously discussed commands are used in the classic makefile syntax.
Now consider how to install GRUB on a partition:
Mkdir -p tempdir # creates a temporary mount / dev / loop2 directory tempdir # mounts the partition in the mkdir directory tempdir / boot # creates the / boot directory on the cp -r section grub tempdir / boot / # copy the grub folder to / boot cp kernel.bin tempdir / # copies the kernel to the root of the sleep partition 1 # wait for Ubuntu umount / dev / loop2 # unmount the temporary folder rm -r tempdir # delete the temporary folder losetup -d / dev / loop2 # unmount the partition
After executing the above commands, the image will be ready to install GRUB’a. The following command installs GRUB in the MBR of the hdd.img disk image.
Echo "device (hd0) hdd.img n root (hd0,0) n setup (hd0) n quitn" | grub --batch 1\u003e / dev / null
Everything is ready for testing!
Step 6. Launch:
To compile, use the command:
Make all
After which the kernel.bin file should appear.
To create a boot disk image, use the command:
Sudo make image
As a result, the hdd.img file should appear.
Now you can boot from the hdd.img disk image. You can verify this with the following command:
Qemu -hda hdd.img -m 32
Qemu-system-i386 -hda hdd.img

To check on a real machine, you need to make dd of this image on a flash drive and boot from it. For example, with this command:
Sudo dd if \u003d. / Hdd.img of \u003d / dev / sdb
Summing up, we can say that as a result of the actions taken, we get a set of sources and scripts that allow us to conduct various experiments in the field of system programming. The first step has been taken towards creating system software such as hypervisors and operating systems.