Introduction 3
1. The concept of information security threat 4
2. Sources of information security threats Russian Federation 9
3. Methods and means of information protection 11
4. Examples of Information Security Threats 14
Conclusion 19
List of sources used 20
Introduction
In recent years, computer technology has become an integral part of our lives. It is quite difficult for people in our time to imagine how they used to do without computers, they are so used to them. With the availability of computers, people also began to actively use the services of the Internet - e-mail, the World Wide Web, Internet banking. Now every morning the average person begins with the standard viewing of the news feed, checking the contents of personal mail, visiting various popular social networks, shopping in online stores, paying for various services, etc. The Internet has slowly but surely become a constant assistant in our everyday life. affairs.
The Internet makes communication easier and breaks down language barriers, now even if your friend lives a thousand kilometers away from you in another city or even in another country, you can communicate with him, if you wish, at least all day long.
But with all the advantages of the Internet, there are many dangers in it. First of all, these are threats to personal and state security. The Internet is a free space where personal data, bank card data can be easily stolen, information wars are waged on the Web, information conflicts are generated.
Thus, the threat to information security is one of the most important problems of modern human life and we need to know where it comes from and how we can protect ourselves.
1. The concept of information security threat
The life of a modern society is unthinkable without modern information technologies... Computers serve banking systems, control the operation of nuclear reactors, distribute energy, keep track of train schedules, control planes and spacecraft. Computer networks and telecommunications predetermine the reliability and power of a country's defense and security systems. Computers provide information storage, processing and provision to consumers, thus realizing information technologies.
However, it is precisely the high degree of automation that generates the risk of reduced security (personal, information, government, etc.). The availability and widespread dissemination of information technologies, computers makes them extremely vulnerable to destructive influences. There are many examples of this.
Under threat to information security means an action or event that can lead to destruction, distortion or unauthorized use information resources, including stored, transmitted and processed information, as well as software and hardware.
The main types of threats to the security of information technology and information (threats to the interests of subjects of information relations) are:
- natural disasters and accidents (flood, hurricane, earthquake, fire, etc.);
- failures and failures of equipment (technical means) AITU;
- consequences of design and development errors of AITU components (hardware, information processing technology, programs, data structures, etc.);
- operational errors (users, operators and other personnel);
- deliberate actions of violators and intruders (offended persons from among the personnel, criminals, spies, saboteurs, etc.).
Security threats can be classified according to various criteria.
According to the results of the action: 1) the threat of leakage; 2) threat of modification; 3) the threat of loss.
Violation of information properties: a) threat of violation of the confidentiality of the information being processed; b) the threat of violation of the integrity of the processed information; c) the threat of a system malfunction (denial of service), i.e., the threat of availability.
By the nature of occurrence: 1) natural; 2) artificial.
Natural threats- these are threats caused by impacts on a computer system and its elements of objective physical processes or natural disasters.
Man-made threats Are threats to the computer system caused by human activity. Among them, based on the motivation of actions, one can single out:
a) unintentional(unintentional, accidental) threats caused by design errors computer system and its elements, errors in software, errors in the actions of personnel, etc .;
b) deliberate(intentional) threats associated with the selfish aspirations of people (intruders). Sources of threats in relation to information technology can be external or internal (components of the computer system itself - its hardware, programs, personnel).
The main unintentional artificial threats (actions performed by people accidentally, through ignorance, inattention or negligence, out of curiosity, but without malicious intent):
- unintentional actions leading to partial or complete rejection system or destruction of hardware, software, information resources of the system (unintentional damage to equipment, deletion, corruption of files from important information or programs, including system ones, etc.);
- illegal switching on of equipment or changing the operating modes of devices and programs;
- unintentional damage to information carriers;
- launching technological programs that, if used incompetently, can cause a loss of system performance (freezing or looping) or irreversible changes in the system (formatting or restructuring of storage media, deleting data, etc.);
- illegal introduction and use of unaccounted programs (game, educational, technological, etc., which are not necessary for the violator to perform his official duties) with the subsequent unreasonable waste of resources (CPU load, seizure random access memory and memory on external media);
- infecting your computer with viruses;
- careless actions leading to the disclosure of confidential information or making it publicly available;
- disclosure, transfer or loss of access control attributes (passwords, encryption keys, identification cards, passes, etc.).
- design of system architecture, data processing technologies, development of application programs with capabilities that pose a threat to system performance and information security;
- ignoring organizational restrictions (established rules) when ranking in the system;
- logging into the system bypassing protection means (loading an extraneous operating system from removable magnetic media, etc.);
- incompetent use, adjustment or unlawful disabling of protective equipment by security personnel;
- sending data to the wrong address of the subscriber (device);
- entering erroneous data;
- unintentional damage to communication channels. c.124]
The main deliberate man-made threats are characterized by possible ways deliberate disruption of work, disabling the system, entering the system and unauthorized access to information:
- physical destruction of the system (by explosion, arson, etc.) or disablement of all or some of the most important components of the computer system (devices, carriers of important system information, personnel, etc.);
- shutdown or failure of subsystems to ensure functioning computing systems(power supply, cooling and ventilation, communication lines, etc.);
- actions to disrupt the functioning of the system (changing the operating modes of devices or programs, strike, sabotage of personnel, setting up powerful active radio interference at the frequencies of the system's devices, etc.);
- the introduction of agents into the number of system personnel (including, possibly, into the administrative group responsible for security);
- recruitment (by bribery, blackmail, etc.) of personnel or individual users with certain powers;
- the use of eavesdropping devices, remote photography and video filming, etc .;
- interception of side electromagnetic, acoustic and other radiation from devices and communication lines, as well as directing active radiation to auxiliary technical means that are not directly involved in information processing (telephone lines, power networks, heating, etc.);
- interception of data transmitted through communication channels and their analysis in order to find out the exchange protocols, the rules for entering the connection and authorizing the user and subsequent attempts to imitate them to penetrate the system;
- theft of information carriers (disks, flash tape, memory chips, storage devices and personal computers);
- unauthorized copying of information carriers;
- theft of industrial waste (printouts, records, discarded media, etc.);
- reading the remnants of information from random access memory and from external storage devices;
- reading information from areas of RAM used by the operating system (including the protection subsystem) or other users, in asynchronous mode, using the disadvantages of multitasking operating systems and programming systems;
- illegal receipt of passwords and other details of access control (by undercover means, using the negligence of users, by selection, imitation of the system interface, etc.) with subsequent disguise as a registered user ("masquerade");
- unauthorized use of user terminals with unique physical characteristics, such as the number of a workstation on the network, physical address, address in the communication system, hardware encryption unit, etc .;
- opening of cryptographic information protection ciphers;
- the introduction of special hardware attachments, "bookmarks" and "viruses" ("Trojan horses" and "bugs") programs, that is, such sections of programs that are not needed for the implementation of the declared functions, but allow to overcome the protection system, secretly and illegally access to system resources in order to register and transfer critical information or disorganize the functioning of the system;
- illegal connection to communication lines for the purpose of working "between the lines", using pauses in the actions of a legitimate user on his behalf, followed by the introduction of false messages or modification of transmitted messages;
- illegal connection to communication lines with the aim of directly substituting a legitimate user by physically disconnecting him after logging in and successfully authenticating, followed by the introduction of misinformation and the imposition of false messages. p.71]
It should be noted that more often than not, the attacker uses more than one method to achieve the set goal, but some combination of the methods listed above.
2. Sources of threats to the information security of the Russian Federation
Sources of threats information security of the Russian Federation are subdivided into external and internal.
TO external sources relate:
- activities of foreign political, economic, military, intelligence and information structures directed against the interests of the Russian Federation in the information sphere;
- the desire of a number of countries to dominate and infringe on Russia's interests in the global information space, to oust it from the external and internal information markets;
- aggravation of international competition for the possession of information technologies and resources;
- activities of international terrorist organizations;
- increasing the technological gap between the leading powers of the world and building up their capabilities to counter the creation of competitive Russian information technologies;
- activities of space, air, sea and ground technical and other means (types) of reconnaissance of foreign states;
- the development by a number of states of concepts of information wars, providing for the creation of means of dangerous impact on the information spheres of other countries of the world, disruption of the normal functioning of information and telecommunication systems, the safety of information resources, obtaining unauthorized access to them. 7, c.15]
TO internal sources relate:
- the critical state of domestic industries;
- an unfavorable crime situation, accompanied by tendencies for the merging of state and criminal structures in the information sphere, for criminal structures to gain access to confidential information, increase the influence of organized crime on the life of society, reduce the degree of protection of the legitimate interests of citizens, society and the state in the information sphere;
- insufficient coordination of the activities of federal bodies of state power, bodies of state power of the constituent entities of the Russian Federation in the formation and implementation of a unified state policy in the field of ensuring information security of the Russian Federation;
- insufficient elaboration of the regulatory legal framework governing relations in the information sphere, as well as insufficient law enforcement practice;
- underdevelopment of civil society institutions and insufficient state control over the development of the information market in Russia;
- insufficient funding of measures to ensure the information security of the Russian Federation;
- insufficient economic power of the state;
- decrease in the efficiency of the education and training system, insufficient number of qualified personnel in the field of information security;
- insufficient activity of federal bodies of state power, bodies of state power of the constituent entities of the Russian Federation in informing society about their activities, in explaining decisions made, in the formation of open state resources and the development of a system of citizens' access to them;
- Russia's lag behind the leading countries of the world in terms of informatization of federal government bodies, government bodies of constituent entities of the Russian Federation and local government bodies, the credit and financial sphere, industry, agriculture, education, health care, services and everyday life of citizens. 9, p. 119 ]
3. Methods and means of information protection
The problem of creating an information security system includes two complementary tasks:
1) development of an information protection system (its synthesis);
2) evaluation of the developed information security system.
The second problem is solved by analyzing it technical characteristics in order to establish whether the information protection system meets the set of requirements for these systems. Such a task is currently being solved almost exclusively by expert means with the help of certification of information security tools and certification of the information security system in the process of its implementation.
Let's consider the main content of modern information protection methods, which form the basis of protection mechanisms.
Obstacles- methods of physically blocking the path of the attacker to the protected information (to equipment, storage media, etc.).
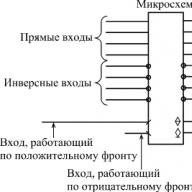
Access control- a method of protecting information by regulating the use of all resources of a computer information system (elements of databases, software and hardware). Access control includes the following security features:
- identification of users, personnel and resources of the system (assigning a personal identifier to each object);
- identification (authentication) of an object or subject by the identifier presented by him;
- authorization check (checking the compliance of the day of the week, time of day, requested resources and procedures with the established regulations);
- permission and creation of working conditions within the established regulations;
- registration (logging) of calls to protected resources;
- registration (alarm, shutdown, delay of work, refusal of the request) in case of attempts of unauthorized actions.
Disguise- a method of protecting information by means of its cryptographic closure. This method is widely used abroad both in processing and in storing information, including on floppy disks. When transmitting information over long-distance communication channels this method is the only reliable one.
Regulation- a method of information protection, creating such conditions for the automated processing, storage and transmission of protected information, in which the possibility of unauthorized access to it would be minimized.
Compulsion- a method of protection, in which users and personnel of the system are forced to comply with the rules for the processing, transfer and use of protected information under the threat of material, administrative or criminal liability.
Motivation- a method of protection that encourages the user and system personnel not to violate the established order by observing the established moral and ethical standards (both regulated and unwritten).
The considered methods of ensuring security are implemented in practice through the use of various means of protection, such as technical, software, organizational, legislative and moral and ethical. K. main means of protection, used to create a security mechanism include the following:
Technical means are implemented in the form of electrical, electromechanical and electronic devices... The entire set of technical means is divided into hardware and physical.
Under hardware it is customary to understand technology or devices that interface with such equipment via a standard interface. For example, a system for identifying and differentiating access to information (by means of passwords, recording codes and other information on various cards).
Physical aids are implemented as stand-alone devices and systems. For example, locks on doors where equipment is located, grates on windows, uninterruptible power supplies, electromechanical burglar alarm equipment.
Software are software specifically designed to perform information security functions. This group of tools includes: an encryption mechanism (cryptography is a special algorithm that is launched by a unique number or bit sequence, usually called an encryption key; then the encrypted text is transmitted over communication channels, and the recipient has his own key for decrypting information), a digital signature mechanism, mechanisms access control, data integrity mechanisms, scheduling mechanisms, routing control mechanisms, arbitration mechanisms, antivirus software, archiving programs (for example, zip, rar, arj, etc.), protection during the input and output of information, etc.
Organizational means protection are organizational, technical and organizational and legal measures carried out in the process of creating and operating computers, telecommunications equipment to ensure the protection of information. Organizational measures cover all structural elements of equipment at all stages of their life cycle (construction of premises, design of a computer information system for banking, installation and adjustment of equipment, use, operation).
Moral and ethical means protections are implemented in the form of all kinds of norms that have developed traditionally or are taking shape with the spread of computing technology and communications in society. For the most part, these norms are not mandatory as legislative measures, but non-compliance with them usually leads to the loss of a person's authority and prestige. The most prominent example of such norms is the US Computer User Association's Code of Professional Conduct.
Legislative means protections are determined by the legislative acts of the country, which regulate the rules for the use, processing and transmission of information of limited access and establish measures of responsibility for violation of these rules.
All considered means of protection are divided into formal (performing protective functions strictly according to a predetermined procedure without direct human participation) and informal (determined by purposeful human activity or regulate this activity).
4. Examples of information security threats
According to a 2015 study by Kaspersky Lab, 36% of Russian users suffered at least one account hack, as a result of which their personal data was stolen, or the profile was used to send malware.
Most often, cybercriminals are interested in accessing an account in social network and e-mail(14%) and a password for online banking (5%).
53% of respondents received phishing messages as a result of hacking or ended up on suspicious sites, the purpose of which was to extract credentials from them. The information stored in the profile was completely destroyed for every fifth victim, and in 14% of cases, personal data was used for criminal purposes, for example, to conduct unauthorized transactions.
Not only the users whose credentials have been stolen, but also their friends and relatives suffer from the actions of cybercriminals. For example, more than half of the victims of account hacking found that someone sent messages on their behalf, and almost every fourth - that their friends clicked on the malicious link received from them.
Despite this, only 28% of users create strong passwords for their accounts and only 25% choose safe ways their storage.
For the year from June 2014 to June 2015, cybercriminals stole 2.6 billion rubles through Internet banking systems, according to the report of Group-IB at the conference "Trends in the development of crimes in the field of high technologies-2015". For the same period last year, the amount was several times higher - 9.8 billion rubles. "We record a decrease in damage with an increase in the number of attacks," said Dmitry Volkov, head of the Bot-Trek Intelligence cyber intelligence service.
The greatest damage was incurred by legal entities that lost 1.9 billion rubles as a result of the actions of cybercriminals. 16 companies become victims of cyberattacks every day, losing an average of 480 thousand rubles. At the same time, hackers have learned to bypass traditional means of protection: neither tokens, nor additional SMS-authentication can save you from "auto-uploads" - Trojans that allow you to transfer money from accounts by substituting details. Confirming a payment, a client infected with such a Trojan sees the correct recipient data, although in reality the money goes to the cybercriminals' account.
As a result of targeted attacks, Russian banks themselves lost 638 million rubles in the reporting period. Even single attacks on clients of large banks bring in a lot of income. The interest of cybercriminals in both trading and broker systems is growing. Thus, in February 2015, the first successful attack on a stock broker in Russia was carried out, which lasted only 14 minutes and resulted in damage of about 300 million rubles.
Almost 100 million rubles. stolen from individuals, and 61 million rubles - with the help of Trojans, sharpened for the Android platform. The Android vulnerability is attracting more and more cybercriminals, according to the report: ten new criminal groups working with Android Trojans have emerged, and the number of incidents has tripled. Every day 70 mobile banking users on Android fall prey to cybercriminals.
According to Group-IB, the development of an ecosystem serving the commission of cybercrimes continues. Services for cashing the stolen money brought cybercriminals 1.92 billion rubles. The turnover of sites trading data on bank cards, logins and passwords different systems: revenue of seven such stores exceeded 155 million rubles.
According to the forecast, next year developers of malicious software will fully focus on mobile platforms, the number of incidents and the amount of theft from individuals will increase due to the interception of card data, logins and passwords for Internet banking on Android devices. In addition, companies will face more big amount incidents with programs that encrypt data for subsequent extortion of money for their decryption (cryptolockers). The number of thefts of information about bank cards through POS-terminals will also grow: more and more programs for these purposes appear, and some of them are in the public domain.
According to a study by the information security company Invincea, over the past few days, experts have discovered 60 cases of infection of systems with Dridex banking malware in France. The malware spreads under the guise of emails with an attached file Microsoft Office that looks like an invoice from a popular hotel or store. The malicious attachment is in French and contains a hexadecimal code.
In 2014, nearly 18 million American citizens became victims of identity theft, with credit cards and bank accounts being targeted in most cases, The Networkworld reports, citing a report from the US Department of Justice.
According to the Bureau of Justice Statistics, over the past year, the number of victims of cyber fraudsters has increased by 1 million compared to 2012. It is worth noting that the agency's report took into account not only cases of personal information being compromised, but also its use to obtain financial or other benefits. According to the data, two out of five incidents involved illegal manipulation of credit cards, and about the same number - with fraud with bank accounts.
The 2015 Financial Impact of Cybercrime Study by the Ponemon Institute (USA) provides data on the annual cost of mitigating the impact of cyber attacks on companies in the United States, the United Kingdom, Japan, Germany, Australia, Brazil and Russia.
The study found that the average cost of cybercrimes in American companies is $ 15 million per year - that is, 82% more than when the study began six years ago. In other words, costs increased by almost 20% every year.
Elimination of the consequences of cyberattacks today requires an average of 46 days (this period has increased by almost 30% in six years), and companies spend an average of $ 1.9 million to eliminate the consequences of each of them.
A US study also found that many businesses are investing in security analytics technologies to avoid the costs of detecting and remediating cyberattacks. This tactic is paying off: the cost of responding to attacks is reduced, and this can significantly increase the return on investment.
Personal data of 1.5 million users were published in cloud service Amazon
The victims of the leak were clients of health insurance companies.
One and a half million Americans have become victims of personal information leaks. Full names, addresses, phone numbers, health and prescription data were mistakenly released to the Amazon cloud by health insurance companies using Systema Software.
The incident affected the Kansas Self-Insurance Fund, CSAC Excess Insurance Authority and the Salt Lake County database in Utah. The cause of the leak and the exact number of victims are still unknown. In total, 1 million users' social security numbers, 5 million financial transaction records, hundreds of thousands of injuries and 4.7 million notes, including those related to fraud investigations, were published.
Conclusion
Based on the results of the studies carried out in this work, the following conclusions can be formulated:
- the life of modern society is unthinkable without modern information technologies;
- in turn, a high degree of automation creates a risk of reduced security (personal, information, government, etc.). The availability and widespread dissemination of information technologies, computers make them extremely vulnerable to destructive influences, and there are many examples of this;
- information security threat is an action or event that can lead to destruction, distortion or unauthorized use of information resources, including stored, transmitted and processed information, as well as software and hardware;
- sources of threats to the information security of the Russian Federation are divided into external and internal;
- to ensure the protection of information, there are a number of methods, as well as means for their implementation;
- According to the Internet magazine Itsec, there was a very high level of various cybercrimes in 2014 and 2015.
The above examples of violations of personal and state information security once again prove that the existing threats can in no case be neglected either by the Internet users themselves, or by organizations and enterprises.
List of sources used
- Domarev V.V. Safety of information technologies. Systematic approach - K .: TID Dia Soft LLC, 2014 .-- 992 p.
- Lapina M.A., Revin A.G., Lapin V.I.Information law. - M .: UNITI-DANA, 2014 .-- 548 p.
- Bartender Scott. Development of information security rules. - M .: Williams, 2012 .-- 208 p.
- Galatenko V. A. Information security standards. - M .: Internet University of Information Technologies, 2006. - 264 p.
- Galitsky A. V., Ryabko S. D., Shangin V. F. Information security in the network. - M .: DMK Press, 2014 .-- 616 p.
- Gafner V.V. Information security: textbook. allowance. - Rostov on Don: Phoenix, 2010 .-- 324 p.
- Information security (2nd book of the socio-political project "Actual problems of social security"). // "Arms and Technologies", No. 11, 2014. - P.15-21.
- Lepekhin A. N. Investigation of crimes against information security. - M .: Tesey, 2008 .-- 176 p.
- Lopatin V.N. Information security of Russia: Man, society, state. - M .: 2010 .-- 428 p.
- Petrenko S. A., Kurbatov V. A. Information security policies. - M .: IT Co., 2014 .-- 400 p.
- Petrenko S. A. Information risk management. - M .: IT Co. Company; DMK Press, 2004 .-- 384 p. - ISBN 5-98453-001-5.
- Shangin V.F.Protection computer information. Effective methods and funds. M .: DMK Press, 2013 .-- 544 p.
- Shcherbakov A. Yu. Modern computer security. Theoretical basis. Prak inform about this to us.
It should be noted that, although the information security problems generated by informatization are global, for Russia they acquire special significance in connection with its geopolitical and economic position.
In the Doctrine of Information Security of the Russian Federation, approved by the President of the Russian Federation on September 9, 2000, threats to the information security of the country, according to their general orientation, are divided into threats:
* constitutional rights and freedoms of man and citizen in the field of information activities;
* the spiritual life of society;
Information Security
* information infrastructure;
* information resources.
Threats to constitutional human and civil rights and freedoms in the field of information security can be:
* the adoption by public authorities of regulatory legal acts that infringe on the constitutional rights and freedoms of citizens in the field of information activities;
* creation of monopolies on the formation, receipt and distribution of information in the Russian Federation, including using telecommunication systems;
* opposition, including from criminal structures, to the exercise by citizens of their constitutional rights to personal and family secrets, secrecy of correspondence, telephone conversations and other messages, as well as ineffective application of the existing regulatory framework in this area;
* irrational, excessive restriction of access to public necessary information;
* violation of constitutional human and civil rights and freedoms in the field of mass media;
* non-compliance by state authorities, organizations and citizens with the requirements of the legislation of the Russian Federation regulating relations in the information sphere.
Threats to the spiritual life of society may be:
* the use of means of influencing the mass consciousness of citizens;
* disorganization and destruction of the system of accumulation and preservation of cultural values, including archives;
* restriction of citizens' access to open state information resources of state authorities, other socially significant information;
* decline in the spiritual, moral and creative potential of Russia;
* manipulation of information (disinformation, concealment or distortion of information).
Threats to information infrastructure may be:
* violation of targeting and timeliness of information exchange, illegal collection and use of information;
* violation of information processing technology;
* introduction into hardware and software products of components that implement functions not provided for in the documentation for these products;
* development and distribution of programs that disrupt the normal functioning of information and information and telecommunication systems, including information security systems;
* destruction, damage, electronic suppression or destruction of means and systems of information processing, telecommunications and communications;
* theft of software or hardware keys and means of cryptographic information protection;
* interception of information in technical channels, its leakage arising from the operation of technical means of processing and storage, as well as during the transfer of information through communication channels;
* introduction of electronic devices for intercepting information in technical means of processing, storing and transmitting information through communication channels, as well as in the office premises of government bodies and organizations;
* destruction, damage, destruction or theft of machine and other media;
* interception, decryption and imposition of false information in data transmission networks, communication lines and mass media systems;
* impact on password-key protection systems automated systems processing and transmission of information;
* purchase abroad of information technologies, informatization means, telecommunications and communications, which have domestic counterparts that are not inferior in their characteristics to foreign models.
Threats to information resources may be:
* activity of space, air, sea and ground technical means of reconnaissance of foreign states;
* implementation of unauthorized access to information resources and their illegal use;
* theft of information resources from libraries, archives, banks and databases;
* violation of legal restrictions on the distribution of information resources.
In his Address on National Security (June 13, 1996), the President of the Russian Federation determined the main threats to Russia in the information sphere in the following way:
* internal - the country's lag behind the leading countries in terms of the level and pace of informatization, the lack of a clearly formulated information policy;
* external - attempts to prevent Russia from participating on equal terms in international information exchange, interference and targeted penetration into the activities and development of the information infrastructure of the Russian Federation, the desire to reduce the use of the Russian language as an international means of communication and, through this, the narrowing of the Russian information space.
These and other internal and external threats by methods of exposure(realizations) are divided into informational, software-mathematical, physical and organizational.
Information Threats are implemented through unauthorized access to information resources and their theft for the purpose of illegal use, negative manipulation of information (disinformation, distortion of information, hiding it), violation of information processing technology, etc.
Mathematical threats are implemented by introducing components into hardware and software systems that perform functions that are not described in the documentation for these systems and reduce the efficiency of their operation, the development and distribution of programs (viruses, Trojan horses, etc.) that disrupt the normal functioning of systems, including information security systems.
Physical threats associated with physical impact (destruction, damage, theft) on information systems and their elements, signal interception of information in transmission channels or in office premises, etc.
TO organizational threats First of all, the weak legal framework for ensuring information security should be attributed. There is practically no legal support for information security at the regional level. The requirements of existing legislative acts (the Constitution of the Russian Federation, the laws of the Russian Federation "On Security", "On State Secrets", "On Information, Informatization and Protection of Information", etc.) are not always met. The shortcomings of the legal system lead to the fact that a significant amount of information with limited access in the financial exchange, tax, customs, foreign economic, housing and other spheres in the form of specific databases is distributed by various commercial firms.
V information space from the point of view of information security, the most typical there are two dangers:
1) control (extraction) of information resources of the state, that is, in fact, information intelligence (espionage). The information space has been and remains the domain of numerous intelligence services. Today, information intelligence can be implemented in two ways: unauthorized entry into information and control systems; legally, due to the active participation of foreign firms in the creation of the information structure of Russia. At the same time, in addition to the negative consequences associated with the fact that the country's information resources are under the control of the relevant foreign structures, direct damage is inflicted on the economy - domestic science and production are left without their own orders;
2) the threat of destruction or disorganization of information resources of elements of state structures. With the current level of development of information technology, such impacts can be carried out even in peacetime. They are fraught with the destruction of valuable information for the state, its distortion or the introduction of negative information in order to disorganize or make wrong decisions at the appropriate level of government.
A special place is occupied by security of computer networks, which allow to combine and share a large amount of information resources of local and global scale. Computer networks are becoming one of the main means of information communication. At the same time, their enormous capabilities come into conflict with the problem of ensuring the protection of information. This circumstance must be taken into account when creating and developing both local and global computer networks. So, in the process of creating the Internet in the United States in January 1981, the Computer Security Center of the Ministry of Defense was created, in 1985 it was transformed into National Center computer security and transferred to the National Security Agency.
Analysis of the above threats, forms and methods of their impact on security objects in the information sphere, as well as methods and means of combating these threats allows us to assert that at present, two directions are already beginning to crystallize in the theory and practice of information security, which can be determined (although rather tentatively) as information and psychological security and information protection.
Information and psychological security - the state of protection of citizens, individual groups and social strata of society, mass associations of people, the population as a whole from negative information and psychological influences carried out in the information space (more on this later).
Protection of information - ensuring information security (countering threats to information infrastructure and information resources).
Currently, the most actively developed problems of information protection: organizational, legal, technical and technological measures to prevent and reflect threats to information resources and systems, eliminate their consequences. The theory of information security is being formed, methods and means of information security are being created and actively used in practice, specialists are being trained in a number of specialties and specializations, such as information security technology, comprehensive information security of automated systems, information security and protection, etc.
10. Expanding the areas of application of information technologies, being a factor in the development of the economy and improving the functioning of public and state institutions, at the same time generates new information threats.
Opportunities for cross-border circulation of information are increasingly being used to achieve geopolitical, military-political, as well as terrorist, extremist, criminal and other illegal goals at the expense of international security and strategic stability.
At the same time, the practice of introducing information technologies without linking to ensuring information security significantly increases the likelihood of information threats.
11. One of the main negative factors affecting the state of information security is the increase in a number of foreign countries opportunities for information technology impact on the information infrastructure for military purposes.
At the same time, the activities of organizations carrying out technical intelligence in relation to Russian state bodies, scientific organizations and enterprises of the military-industrial complex are intensifying.
12. The scale of the use by the special services of individual states of means of providing information and psychological influence aimed at destabilizing the internal political and social situation in various regions of the world and leading to the undermining of sovereignty and violation of the territorial integrity of other states is expanding. Religious, ethnic, human rights and other organizations, as well as individual groups of citizens are involved in this activity, while the opportunities of information technologies are widely used.
There is a tendency towards an increase in the volume of materials in foreign mass media containing a biased assessment of the state policy of the Russian Federation. Russian media are often subjected to open discrimination abroad, and obstacles are created for Russian journalists to carry out their professional activities.
The informational impact on the population of Russia, primarily on young people, is growing in order to erode traditional Russian spiritual and moral values.
13. Various terrorist and extremist organizations widely use mechanisms of informational influence on individual, group and public consciousness in order to whip up interethnic and social tension, incite ethnic and religious hatred or enmity, propagate extremist ideology, as well as attract new supporters to terrorist activities. For illegal purposes, such organizations are actively creating means of destructive influence on objects of critical information infrastructure.
14. The scale of computer crime is increasing, primarily in the credit and financial sphere, the number of crimes related to the violation of constitutional human and civil rights and freedoms, including those related to the inviolability of private life, personal and family secrets, in the processing of personal data is increasing. using information technology. At the same time, the methods, methods and means of committing such crimes are becoming more sophisticated.
15. The state of information security in the field of national defense is characterized by an increase in the use by individual states and organizations of information technologies for military-political purposes, including for the implementation of actions contrary to international law, aimed at undermining the sovereignty, political and social stability, territorial integrity of the Russian Federation and her allies and the threat international peace, global and regional security.
16. The state of information security in the field of state and public security is characterized by a constant increase in complexity, an increase in the scale and an increase in the coordination of computer attacks on critical information infrastructure facilities, an increase in intelligence activities of foreign states in relation to the Russian Federation, as well as an increase in threats of the use of information technologies for the purpose of causing damage sovereignty, territorial integrity, political and social stability of the Russian Federation.
17. The state of information security in the economic sphere is characterized by an insufficient level of development of competitive information technologies and their use for the production of goods and the provision of services. The level of dependence of the domestic industry on foreign information technologies remains high in terms of the electronic component base, software, computers and communication facilities, which determines the dependence of the socio-economic development of the Russian Federation on the geopolitical interests of foreign countries.
18. The state of information security in the field of science, technology and education is characterized by insufficient efficiency scientific research aimed at creating promising information technologies, a low level of implementation of domestic developments and insufficient staffing in the field of information security, as well as low awareness of citizens in matters of personal information security. At the same time, measures to ensure the security of information infrastructure, including its integrity, availability and sustainable operation, using domestic information technologies and domestic products often do not have an integrated framework.
19. The state of information security in the field of strategic stability and equitable strategic partnership is characterized by the desire of individual states to use technological superiority to dominate the information space.
The current distribution between countries of the resources necessary to ensure the safe and stable operation of the Internet does not allow for the implementation of joint fair, trust-based management of them.
The absence of international legal norms regulating interstate relations in the information space, as well as mechanisms and procedures for their application, taking into account the specifics of information technologies, complicates the formation of an international information security system aimed at achieving strategic stability and equal strategic partnership.
Sources of threats to the information security of the Russian Federation are divided into external and internal. External sources include:
- - activities of foreign political, economic, military, intelligence and information structures directed against the interests of the Russian Federation in the information sphere;
- - the desire of a number of countries to dominate and infringe on Russia's interests in the global information space, to oust it from the external and internal information markets;
- - aggravation of international competition for the possession of information technologies and resources;
- - activities of international terrorist organizations;
- - increasing the technological gap between the leading powers of the world and building up their capabilities to counteract the creation of competitive Russian information technologies;
- - activities of space, air, sea and ground technical and other means (types) of reconnaissance of foreign states;
- - the development by a number of states of concepts of information wars and related weapons, providing for the creation of means of dangerous influence on the information spheres of other countries of the world, disruption of the normal functioning of information and telecommunication systems, the safety of information resources, and obtaining unauthorized access to them.
Internal sources include:
- - the critical state of domestic industries;
- - an unfavorable crime situation, accompanied by tendencies for the merging of state and criminal structures in the information sphere, for criminal structures to gain access to confidential information, increase the influence of organized crime on the life of society, reduce the degree of protection of the legitimate interests of citizens, society and the state in the information sphere;
- - insufficient coordination of the activities of federal bodies of state power, bodies of state power of the constituent entities of the Russian Federation in the formation and implementation of a unified state policy in the field of ensuring the information security of the Russian Federation;
- - insufficient elaboration of the legal framework governing relations in the information sphere, as well as insufficient law enforcement practice;
- - underdevelopment of civil society institutions and insufficient state control over the development of the information market in Russia;
- - insufficient funding of measures to ensure
- - insufficient economic power of the state;
- - a decrease in the efficiency of the education and training system, an insufficient number of qualified personnel in the field of information security;
- - insufficient activity of federal bodies of state power, bodies of state power of the constituent entities of the Russian Federation in informing society about their activities, in explaining decisions made, in the formation of open state resources and the development of a system of citizens' access to them;
- - Russia's lag behind the leading countries of the world in terms of informatization of federal government bodies, government bodies of the constituent entities of the Russian Federation and local government bodies, the credit and financial sphere, industry, agriculture, education, health care, services and everyday life of citizens.
With the transition from an industrial society to information and the corresponding development of information technologies, considerable attention is paid to the latest types of so-called "humane weapons" ("non-lethal types of weapons and technologies of war"). These include information, psychotronic, economic, conscientious weapons and ir. A special place among them is occupied by information weapons and information warfare technologies. Their importance is evidenced by the fact that the United States has created information troops and for the third year in a row cyber warfare units are being produced. Today, US Department of Defense directives detail how to prepare for information warfare. In terms of their effectiveness, information weapons are comparable to weapons of mass destruction. The spectrum of action of information weapons can range from causing harm to the mental health of people to introducing viruses into computer networks and destroying information. The Pentagon on supercomputers simulates variants of possible wars in the XXI century using methods and technology of "non-lethal weapons".
In the armed forces of NATO, especially the United States, considerable attention is paid to the role of "non-lethal weapons" and technologies, primarily information weapons and psychological and propaganda operations in the wars of the 21st century, which significantly change the nature of the use of land, air and naval forces in theater of operations. and geopolitical and civilizational confrontation between the main centers of the emerging multipolar world.
The difference between the types and technologies of "lethal weapons" from conventional military weapons is that they focus on the use of algorithms and technologies that concentrate basic knowledge aimed at defeating the enemy. Information warfare essentially personifies the war of civilizations for survival in the face of constantly dwindling resources. Information weapon affects the human consciousness, destroys the methods and forms of personality identification in relation to fixed communities, it transforms the individual's memory matrix, creating a personality with predetermined parameters (type of consciousness, artificial needs, forms of self-determination, etc.) that satisfy the requirements of the aggressor, disables the control system of the enemy state and its armed forces.
Practice has shown that the greatest losses are incurred by the armed forces from the use of "non-force" information weapons against them and, first of all, from the impact of damaging elements acting on control systems and the human psyche. Information and conscientious weapons affect “ideal” objects (sign systems) or their material carriers.
Currently, a global information, cultural and informational and ideological expansion of the West is being carried out through world telecommunication networks (for example, the Internet) and through the mass media. Many countries are forced to take special measures to protect their fellow citizens, their culture, traditions and spiritual values from alien informational influence. There is a need to protect national information resources and preserve the confidentiality of information exchange on the world's open networks, since on this basis, political and economic confrontation of states, new crises in international relations may arise. Therefore, information security, information warfare and information weapons are now in the center of everyone's attention.
Information weapons are means:
- - destruction, distortion or theft of information arrays;
- - overcoming protection systems;
- - restrictions on the admission of legitimate users;
- - disorganization of the work of technical means, computer
Attacking information weapons today can be called:
- - computer viruses that can multiply, be embedded in programs, transmitted through communication lines, data networks, disable control systems, etc .;
- - logic bombs - software embedded devices that are introduced in advance into information and control centers of military or civilian infrastructure, so that on a signal or in set time put them into action;
- - means of suppression of information exchange in telecommunication networks, falsification of information in the channels of state and military administration;
- - means of neutralizing test programs;
- - various kinds of errors deliberately introduced by the enemy into the software of the object.
The versatility, secrecy, multivariance of forms of software and hardware implementation, radical impact, sufficient choice of time and place of use, and finally, cost-effectiveness make information weapons extremely dangerous: they are easily disguised as means of protection, for example, intellectual property; it even allows offensive operations to be conducted anonymously, without declaring war.
The normal life of a social organism is entirely determined by the level of development, the quality of functioning and the security of the information environment. Production and management, defense and communications, transport and energy, finance, science and education, mass media - everything depends on the intensity of information exchange, completeness, timeliness, and reliability of information. It is the information infrastructure of society that is the target of information weapons. But first of all, the new weapon is aimed at the armed forces, defense enterprises, structures responsible for the country's external and internal security. The high degree of centralization of the structures of state management of the Russian economy can lead to disastrous consequences as a result of information aggression. The rate of improvement of information weapons (as, indeed, of any type of attacking weapon) exceeds the rate of development of protection technologies. Therefore, the task of neutralizing information weapons, repelling the threat of their use should be considered as one of the priority tasks in ensuring the national security of the country.
The report of the Joint Security Commission, created by order of the Secretary of Defense and the Director of the CIA in the United States in June 1993 and completed its work in February 1994, states: “... It is already recognized that data networks are becoming the battlefield of the future. Information weapons, the strategy and tactics of which have yet to be carefully developed, will be used with "electronic speed" in defense and attack. Information technology will make it possible to ensure the resolution of geopolitical crises without firing a single shot. Our national security policy and procedures for its implementation should be aimed at protecting our capabilities in conducting information wars and at creating all the necessary conditions to prevent the opposing states from waging such wars ... ".
The destruction of certain types of consciousness presupposes the destruction and reorganization of the communities that constitute this type of consciousness.
There are five main ways of defeating and destroying consciousness in a consistent war:
- 1. The defeat of the neuro-cerebral substrate, which reduces the level of consciousness functioning, can occur on the basis of the action of chemicals, prolonged poisoning of the air, food, directed radiation effects;
- 2. Lowering the level of organization of the information and communication environment on the basis of its disintegration and primitivization, in which consciousness functions and "lives";
- 3. Occult influence on the organization of consciousness on the basis of directed transmission of thought forms to the subject of defeat;
- 4. Special organization and dissemination through communication channels of images and texts that destroy the work of consciousness (conditionally can be designated as a psychotropic weapon);
- 5. Destruction of the methods and forms of personality identification in relation to fixed communities, leading to a change in the forms of self-determination and to depersonalization.
First of all, this type of influence on the change and transformation of the types of image-identifications (deep identification with a goy or another position presented in a specific way) and authentications (feelings of personal authenticity) is carried out by the media, and above all, television. It is in this area that all the main actions to destroy the Russian-Russian post-Soviet consciousness are taking place today.
The ultimate goal of using the conscientious weapon of the ego is the withdrawal of people from the established forms of communalities. The destruction of a people and its transformation into a population occurs due to the fact that no one wants to associate and correlate themselves with the polyethnos to which they previously belonged. Destruction of the established image-identifications is aimed at destroying the mechanisms of human inclusion in naturally formed and existing communities and replacing these evolutionarily naturally formed communities with one completely artificial community of viewers around the TV. It does not matter how a person treats what he sees and hears from the TV screen, it is important that he was a constant viewer, since in this case he can be targeted and sustainably influenced. But in the context of formal peace and the so-called local wars, conscientious war is very effective.
RF IS Doctrine It is a set of official views on the goals, objectives, principles and main directions of ensuring information security "of Russia, serves as the basis for the" formation of state policy "in the field of information (September 9, 2000. Russian President Vladimir Putin approved the" Doctrine of information security of the Russian Federation. ")
The doctrine includes a list of the main types possible threats to information security, which are also associated with telecommunication systems. These threats include:
Displacement from the domestic market of Russian manufacturers of information technology, telecommunications and communications;
The inability of enterprises of national branches of the electronic industry to produce competitive science-intensive products on the basis of the latest achievements of microelectronics, advanced information technologies, allowing to ensure a sufficient level of technological independence of Russia from foreign countries, which leads to the forced widespread use of imported software and hardware in the creation and development of information infrastructure in Russia ;
Increased outflow of specialists and intellectual property rights holders abroad;
Violation of the established regulations for the collection, processing and transmission of information, deliberate actions and errors of personnel of information and telecommunication systems, failure of technical means and software failures in information and telecommunication systems;
Use of means and systems of informatization and communication not certified in accordance with security requirements, as well as means of information protection and control of their effectiveness;
Under information security RF understands the state of protection of its national interests in the information sphere. National interests are a set of balanced interests of an individual, society and state. There is always a potential threat to information security.
RF IS Doctrine represents a set of official views on the goals, objectives, principles and main directions of ensuring information security "of Russia, serves as the basis for" shaping state policy "in the field of information (September 9, 2000, Russian President Vladimir Putin approved the" Doctrine of information security of the Russian Federation. " )
By its focus threats to the information security of the Russian Federation are divided into the following types:
1. Threats to the constitutional rights and freedoms of man and citizen in the field of spiritual life and information activities:
Creation of monopolies on the formation, receipt and dissemination of information;
Restriction of access to information;
Destruction of the system of accumulation and preservation of cultural property, including archives;
The ousting of Russian news agencies and mass media from the internal information market and the strengthening of the dependence of the spiritual, economic and political spheres of public life in Russia on foreign information structures;
Manipulation of information (disinformation, concealment or distortion of information), etc.
2. Threats to information support of the state policy of the Russian Federation:
Monopolization of the information market in Russia;
Low efficiency of information support of the state policy of the Russian Federation due to a shortage of qualified personnel, the absence of a system for the formation and implementation of state information policy;
Violation of the established regulations for the collection, processing and transmission of information, deliberate actions and errors of personnel of information and telecommunication systems, failure of technical means and software failures in information and telecommunication systems, etc.
3. Threats to the development of the domestic information industry:
Counteracting the access of the Russian Federation to the latest information technologies;
Purchase by state authorities of imported means of informatization, telecommunications and communications in the presence of domestic analogues that are not inferior in their characteristics to foreign models;
Increase in the outflow of specialists and intellectual property rights holders abroad, etc.
4. Threats to the security of information and telecommunication facilities and systems:
Illegal collection and use of information;
Violations of information processing technology;
Impact on password-key systems for protecting systems;
Leakage and interception of information through technical channels;
Unauthorized access to information in banks and databases;
Involvement in work on the creation, development and protection of information and telecommunication systems of organizations and firms that do not have state licenses to carry out these types of activities.