By default on all Windows operating systems for protocol connections RDP( Remote Desktop Protocol / Remote Desktop ) uses port TCP 3389 .
If your computer is connected directly to the Internet (for example, a VDS server), or you have configured port 3389/RDP on your edge router to the local network on a Windows computer or server, you can change the standard RDP port 3389 to any other. By changing the RDP port number for connection, you can hide your RDP server from port scanners, reduce the likelihood of exploiting RDP vulnerabilities (the last critical vulnerability in RDP BlueKeep is described in), reduce the number of remote password guessing attempts via RDP (does not forget periodically), SYN and others types of attacks (especially when).
Replacing the standard RDP port can be used when there are several Windows computers behind a router with one white IP address, to which you need to provide external RDP access. On each computer, you can configure a unique RDP port and configure port forwarding on the router to local computers (depending on the RDP port number, the session is redirected to one of the internal PCs).
When choosing a non-standard port number for RDP, please note that it is advisable not to use port numbers in the range 1 to 1023 (known ports) and dynamic ports in the RPC range (49152 to 65535).
Let's try to change the port on which the Remote Desktop service listens for connections to 1350 . For this:
- Open registry editor and go to branch HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp;
- Find DWORD registry setting named PortNumber. This parameter specifies the port on which the Remote Desktop service listens for connections;
- Change the value of this port. I changed the RDP port to 1350 in decimal value (Deciamal);
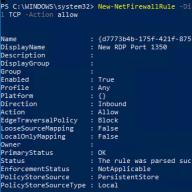
- If Windows Firewall is enabled on your computer, you must create a new rule to allow incoming connections on the new RDP port (if you reconfigure the remote server via RDP without creating a firewall rule, you will lose access to the server). You can create an allow inbound rule for a new RDP TCP/UDP port manually from the ‘Windows Defender Firewall’ console ( firewall.cpl) or with: New-NetFirewallRule -DisplayName "New RDP Port 1350" -Direction Inbound -LocalPort 1350 -Protocol TCP -Action allow AND: New-NetFirewallRule -DisplayName "New RDP Port 1350" -Direction Inbound -LocalPort 1350 -Protocol UDP -Action allow

- Restart the computer or restart the Remote Desktop Service with the command: net stop termservice & net start termservice

- Now, to connect to this Windows computer via RDP, in the mstsc.exe client, you need to specify the RDP connection port separated by a colon as follows: Your_Computer_Name:1350 or by IP address 192.168.1.100:1350 or from the command line: mstsc.exe /v 192.168.1.100 :1350

If you use the RDP connection manager to manage multiple RDP connections, you can specify the RDP port number you set for the connection on the “Connection Settings” tab.

- As a result, you will successfully connect to the desktop of the remote computer on the new RDP port number (use the nenstat –na | Find “LIST” command to verify that the RDP service is now listening on a different port).

The complete PowerShell script to change the RDP port, create a firewall rule, and restart the RDP service on the new port might look like this:
New-NetFirewallRule -DisplayName "New RDP Port $RDPPort" -Direction Inbound –LocalPort $RDPPort -Protocol UDP -Action Allow
Write-host "RDP port number changed to $RDPPort " -ForegroundColor Magenta
You can change the RDP number remotely on multiple computers in an AD domain (specific OU) using Invoke-Command and :
Write-host "Specify the new RDP port number: " -ForegroundColor Yellow -NoNewline;$RDPPort = Read-Host
$PCs = Get-ADComputer -Filter * -SearchBase "CN=DMZ,CN=Computers,DC=winitpro,DC=en"
Foreach ($PC in $PCs) (
Invoke-Command -ComputerName $PC.Name -ScriptBlock (
param($RDPPort)
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-TCP\" -Name PortNumber -Value $RDPPort
New-NetFirewallRule -DisplayName "New RDP Port $RDPPort" -Direction Inbound –LocalPort $RDPPort -Protocol TCP -Action Allow
New-NetFirewallRule -DisplayName "New RDP Port $RDPPort" -Direction Inbound –LocalPort $RDPPort -Protocol TCP -Action Allow
Restart-Service termservice -force
}
This instruction for changing the standard RDP port is suitable for any version of Windows, from Windows XP (Windows Server 2003) to Windows 10 (Windows Server 2019).
Good afternoon, dear readers and guests of the blog, today we have the following task: change the incoming port of the RDP service (terminal server) from the standard 3389 to some other one. Let me remind you that the RDP service is a functionality of Windows operating systems, thanks to which you can open a session over the network to the computer or server you need using the RDP protocol, and be able to work behind it, as if you were sitting at it locally.
What is RDP protocol
Before changing something, it would be good to understand what it is and how it works, I keep repeating this to you. RDP or Remote Desktop Protocol is a remote desktop protocol for Microsoft Windows operating systems, although its origins are from PictureTel (Polycom). Microsoft just bought it. Used for remote work of an employee or user with a remote server. Most often, such servers carry the role of a terminal server, on which special licenses are allocated, either per user or per device, CAL. Here the idea was this, there is a very powerful server, why not share its resources, for example, under the 1C application. This is especially true with the advent of thin clients.
The world saw the terminal server itself, already in 1998 in the Windows NT 4.0 Terminal Server operating system, to be honest, then I didn’t know what it was, and in Russia at that time we all played dandy or sega. RDP connection clients are currently available in all versions of Windows, Linux, MacOS, Android. The most modern version of the RDP protocol at the moment is 8.1.
default rdp port
I’ll immediately write the default rdp port 3389, I think all system administrators know it.
How the rdp protocol works
And so we understood why we came up with the Remote Desktop Protocol, now it is logical that you need to understand the principles of its operation. Microsoft distinguishes two modes of the RDP protocol:
- Remote administration mode > for administration, you get to the remote server and configure and administer it
- Terminal Server mode > to access the Application Server, Remote App or share it for work.

In general, if you install Windows Server 2008 R2 - 2016 without a terminal server, then by default it will have two licenses, and two users will be able to connect to it at the same time, the third will have to throw someone out to work. In client versions of Windows, there is only one license, but this can also be circumvented, I talked about this in the article terminal server on windows 7. Also, Remote administration mode, you can cluster and balance the load, thanks to NLB technology and the Session Directory Service connection server server. It is used to index user sessions, thanks to this server, the user can log in to the remote desktop of terminal servers in a distributed environment. The licensing server is also a mandatory component.

The RDP protocol works over a TCP connection and is an application protocol. When the client establishes a connection with the server, an RDP session is created at the transport layer, where encryption methods and data transfer methods are negotiated. When all negotiations have been determined and initialization is complete, the terminal server sends graphical output to the client and waits for input from the keyboard and mouse.

Remote Desktop Protocol supports multiple virtual channels within a single connection, thanks to which you can use additional functionality
- Send your printer or COM port to the server
- Redirect your local drives to the server
- Clipboard
- Audio and video


RDP connection steps
- Establishing a connection
- Negotiate Encryption Options
- Server authentication
- Negotiation of RDP session parameters
- Client Authentication
- RDP session data
- Breaking an RDP session

Security in the RDP protocol
Remote Desktop Protocol has two authentication methods, Standard RDP Security and Enhanced RDP Security, and we'll look at both in more detail below.
Standard RDP Security
The RDP protocol, with this authentication method, encrypts the connection using the RDP protocol itself, which is in it, using this method:
- When your operating system starts, it generates a pair of RSA keys
- Proprietary Certificate is being generated
- After that, the Proprietary Certificate is signed with the RSA key created earlier
- Now the RDP client connecting to the terminal server will receive a Proprietary Certificate
- The client looks at it and checks it, then receives the server's public key, which is used at the stage of negotiating encryption parameters.
If we consider the algorithm by which everything is encrypted, then this is the RC4 stream cipher. Keys of different lengths from 40 to 168 bits, it all depends on the edition of the Windows operating system, for example, in Windows 2008 Server - 168 bits. Once the server and client have decided on the key length, two new different keys are generated to encrypt the data.
If you ask about data integrity, then here it is achieved through the MAC (Message Authentication Code) algorithm based on SHA1 and MD5
Enhanced RDP Security
The RDP protocol uses two external security modules for this authentication method:
- CredSSP
- TLS 1.0
TLS has been supported since version 6 of RDP. When you use TLS, the encryption certificate can be created using the terminal server, a self-signed certificate, or selected from the store.
When you use the CredSSP protocol, it is a symbiosis of Kerberos, NTLM and TLS technologies. With this protocol, the check itself, in which permission to enter the terminal server is checked, is carried out in advance, and not after a full RDP connection, and thus you save the resources of the terminal server, plus there is more reliable encryption and you can do a single login (Single Sign On ), thanks to NTLM and Kerberos. CredSSP is only available in OS not lower than Vista and Windows Server 2008. Here is this checkbox in the system properties
Allow connections only from computers running Remote Desktop with Network Level Authentication.

Change rdp port
In order to change the rdp port, you will need:
- Open the registry editor (Start -> Run -> regedit.exe)
- Let's move on to the next section:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
Find the PortNumber key and change its value to the port number you need.

Be sure to select a decimal value, for example I will put port 12345.

Once you have done this, then restart the Remote Desktop Service, through the command line, with the following commands:



And we create a new incoming rule for the new rdp port. I remind you that the default rdp port is 3389.

We choose that the rule will be for the port

We leave the protocol as TCP and specify the new RDP port number.

We will have a rule allowing RDP connection on a non-standard port

If necessary, set the necessary network profiles.

Well, let's call the rule in a language that is understandable to ourselves.

Hello everyone, we continue to consider the topic of pro. Today we will look at the built-in Windows tool that allows you to connect to a remote PC. This tool is called RDP (Remote Desktop Protocol) client, if translated into Russian - remote desktop protocol. Using this protocol, you can control a remote computer running the terminal connection service. The RDP client appeared in Windows XP and is still supported in new versions of the operating system. Most likely, many of you do not even know what it is, but with the help of this tool, you can easily connect to a remote computer and manage it. In the article, I will tell you in detail how to connect to a remote desktop on a local network. Therefore, read the text in full.
Preparation before using the RDP client.
In most cases, the RDP client is used when working on the same local network. For example, in order to connect from one computer to another at home, they must be connected to the same router. It is also possible to connect to a remote computer via the Internet, but this is a more complicated configuration method, I think we will analyze this topic in a separate article.
The first thing to do in order to connect via Remote Desktop Protocol is to know the IP address of the remote computer. As a rule, if the network connection on your computers is configured automatically, then with each reboot of the operating system, the IP addresses will change. Therefore, first of all, we set static addresses for all devices on your local network. But first, you need to see what addresses the computer receives automatically. For this . We write the “ipconfig” command and see which: network mask, subnet mask and gateway the network card receives with automatic settings.

Note! As a rule, on all routers, by default, the network mask looks like (192.168.0. or 192.168.1.), respectively, we write all the lines as shown in the screenshot and save the changes.
That's it, now we have set a static IP address for our computer, this will allow us to easily use the RDP client.
How to give permission to connect to a remote desktop.
After we figured out the addresses of computers. Let's move on to enabling the Remote Desktop Protocol feature. These steps must be performed on the computer to which you want to connect. To make it work, follow the steps:

We have completed all the preparatory steps so that the RDP client can earn money with us. Let's now proceed directly to the consideration of the connection process.
We connect to a remote computer via RDP.
In the previous paragraphs, we have dealt with the settings that must be made to work via the remote desktop protocol. Now let's look at how to connect.
Note! We will use the standard Windows tool. Accordingly, we do not have to download any third-party utilities, everything we need will be at our fingertips.
In order to launch the Remote Desktop Connection tool, open the menu "Start" - "All Programs" - "Accessories - Windows". In the menu item that opens, we launch the RDP client and see a field called "Computer". You must enter the address of the remote computer into it, i.e. the one on which we set the static IP address. After clicking on the connect button, the program will ask you to enter "Login and password" to connect to a remote PC. 
You can also open additional settings, for this, open the "Show options" item. Here you can immediately specify the user of the remote computer, configure local resources, as well as screen settings. But I think it's better to leave everything by default and start managing a remote PC.
RDP client - pros and cons.
To be honest, I do not have to use the RDP client so often, but sometimes it is simply necessary. For myself, I have identified the following advantages:
- In order to connect to a remote PC, you do not need to search and install any programs. Everything is provided by Microsoft developers and the tool is built into the operating system;
- Using Remote Desktop, you can get full access to your computer. That allows you to perform any action on it;
- Unlimited time access to a remote PC.
On this, the pluses end, let's move on to the minuses of using this utility:
- The program works correctly only in the local network, in order to set up a connection via the Internet, you need to go into the router settings to forward the port, which is a problem for many users;
- If you are using a VPN, then in order to connect to a remote computer using an RDP client, you need a good internet speed, otherwise you will be watching a slide show;
- The program has a minimal set of functions, and also does not have a built-in file manager, so there is no way to transfer files;
Let's summarize.
Today we reviewed the RDP client for Windows. This tool for remotely connecting to a computer can be considered as an alternative to third-party programs, such as, but RDP is unlikely to be able to completely replace them. Since the built-in tool does not even have all the necessary set of functions that are characteristic of remote access programs. The speed of work leaves much to be desired, but it is perfect in cases where there is no opportunity and time to search for and install other programs and you urgently need to access a remote PC.
Quite often, many users who use remote access sessions have a question about how to change the RDP port. Now let's look at the simplest solutions, and also indicate several main steps in the configuration process.
What is the RDP protocol for?
First, a few words about RDP. If you look at the decoding of the abbreviation, you can understand that remote access
In simple terms, this is a terminal server or workstation tool. Windows settings (and any version of the system) use default settings that are suitable for most users. However, sometimes it becomes necessary to change them.
Standard RDP port: should it be changed?
So, regardless of Windows modification, all protocols have a preset value. This is RDP port 3389, which is used to carry out a communication session (connecting one terminal to remote ones).
What is the reason for the situation when the standard value needs to be changed? First of all, only with the security of the local computer. After all, if you figure it out, with a standard port installed, in principle, any attacker can easily penetrate the system. So now let's see how to change the default RDP port.
Changing settings in the system registry
We note right away that the change procedure is carried out exclusively in manual mode, and any reset or setting of new parameters is not provided in the remote access client itself.

First, we call the standard registry editor with the regedit command in the Run menu (Win + R). Here we are interested in the HKLM branch, in which we need to go down the partition tree through the terminal server directory to the RDP-Tcp directory. In the window on the right we find the key PortNumber. We need to change its meaning.
We go into editing and see 00000D3D there. Many are immediately perplexed about what it is. And this is just the hexadecimal representation of the decimal number 3389. To specify the port in decimal form, we use the appropriate display string for the value representation, and then specify the parameter we need.

After that, we reboot the system, and when we try to connect, we specify a new RDP port. Another way to connect is to use the special command mstsc /v:ip_address:XXXXX, where XXXXX is the new port number. But that's not all.
Windows firewall rules
Alas, the built-in Windows firewall can block the new port. So, you need to make changes to the settings of the firewall itself.

We call the firewall settings with advanced security options. Here you should first select incoming connections and click on the line for creating a new rule. Now we select the item for creating a rule for the port, then we enter its value for TCP, then we allow the connection, we leave the profile section unchanged and finally give the new rule a name, after which we press the button to complete the settings. It remains to reboot the server and, when connecting, specify the new RDP port separated by a colon in the corresponding line. In theory, there shouldn't be any problems.
RDP port forwarding on the router
In some cases, when a wireless connection is used rather than a cable connection, it may be necessary to do port forwarding on the router (router). There is nothing difficult in this.
First, in the system properties, we allow and specify users who have the right to do so. Then we go to the router settings menu through the browser (192.168.1.1 or at the end 0.1 - it all depends on the router model). In the field (if the main address is 1.1), it is desirable to indicate the address, starting from the third (1.3), and write the rule for issuing the address for the second (1.2).
Then, in network connections, we use the details view, where you should view the details, copy the physical MAC address from there and paste it into the router settings.

Now, in the NAT settings section on the modem, enable the connection to the server, add a rule and specify the XXXXX port that needs to be forwarded to the standard RDP port 3389. Save the changes and reboot the router (the new port will not be accepted without a reboot). You can check the connection on some specialized site like ping.eu in the port testing section. As you can see, everything is simple.
Finally, note that the port values are distributed as follows:
- 0 - 1023 - ports for low-level system programs;
- 1024 - 49151 - ports allocated for private purposes;
- 49152 - 65535 - dynamic private ports.
In general, many users usually choose RDP ports from the third range of the list to avoid problems. However, both specialists and experts recommend using these values in tuning, since they are suitable for most of the tasks.
As for exactly this procedure, it is used mainly only in cases of Wi-Fi connection. As you can already see, with a regular wired connection, it is not required: just change the values of the registry keys and add rules for the port in the firewall.
Network Layer Security (SSL) RDP is unfortunately not widely adopted by system administrators who prefer to secure terminal connections in a different way. Perhaps this is due to the apparent complexity of the method, but this is not so, in this material we will consider how to organize such protection simply and without difficulty.
What are the benefits of securing RDP with SSL? First, strong channel encryption, certificate-based server authentication, and network-level user authentication. The latter feature is available starting with Windows Server 2008. Network Level Authentication improves the security of the Terminal Server by allowing the authentication to occur before the session even starts.
Network Level Authentication occurs before connecting to Remote Desktop and displaying the login screen, which reduces the load on the server and greatly increases its protection against intruders and malware, as well as reduces the likelihood of denial of service attacks.
To take full advantage of RDP over SSL, client PCs must be running Windows XP SP3, Windows Vista, or Windows 7 and use RDP client version 6.0 or later.
When using Windows Server 2003 SP1 and later, SSL (TLS 1.0) channel encryption and server authentication will be available, client PCs must have RDP client version 5.2 or later.
In our article, we will consider setting up a terminal server based on Windows Server 2008 R2, however, everything said will be true for Windows Server 2003 (except for the missing features).
For the successful implementation of this solution, your network must have a working certificate authority, the configuration of which we considered in. To trust the certificates issued by this CA on the terminal server, you must install the CA certificate (or chain of certificates) in the .
You should then request a server authentication certificate with the following parameters:
Name - the full name of the terminal server (i.e. server.domain.com if the server belongs to the domain.com domain)
- Certificate type - Server authentication certificate
- Set option Create a new set of keys
- CSP- Microsoft RSA Channel Cryptographic Provider.
- Check box Mark key as exportable.
- For an enterprise CA, check the box Use the computer's local storage for the certificate. (This option is not available in a standalone CA.)
Send a request to the CA and install the issued certificate. This certificate must be installed in the computer's local store, otherwise it will not be able to be used by Terminal Services. To check this, run the console MMC (Start - Run - mmc) and add snap Certificates(File - Add or remove snap-in) for the computer account.
In console root select click View - Options and set view mode Organize certificates by purpose. The issued certificate must be in the group Server authentication.
If you received the certificate using a standalone (standalone) CA (the network does not have a domain structure), then by default it will be installed in the user account store and you will have to perform a number of additional steps.
open Internet Explorer - Internet Options - Content - Certificates, the issued certificate must be installed in the store Personal.
Do an export. When exporting, specify the following options:
- Yes, export private key
- Delete private key after successful export
Then delete the certificate from this store. in a snap Certificates (local computer) Choose a section Server authentication, right click on it All Tasks - Import and import the certificate.
Now in Administration - Remote Desktop Services open Remote Desktop Session Host Configuration(in Windows Server 2003 Administrative Tools - Configuring Terminal Services).
Select the required connection and open its properties. Click the button at the very bottom Choose and select the certificate obtained in the previous step (in Windows Server 2003 this window looks a little different).
 After selecting the certificate, specify the rest of the properties:
After selecting the certificate, specify the rest of the properties:

- Security level SSL
- Encryption level High or FIPS-compatible
- Check box Only allow connections from computers...(not available on Windows Server 2003)
Save the entered parameters, this completes the server setup.
On the client PC, create a remote desktop connection, use the fully qualified server name that is specified in the certificate as the address. Open the connection properties and on the tab Connection - Server Authentication set option Warn.
 In order for this PC to trust the certificates issued by our certificate authority, do not forget to install a CA certificate on it in the store Trusted Root Certification Authorities.
In order for this PC to trust the certificates issued by our certificate authority, do not forget to install a CA certificate on it in the store Trusted Root Certification Authorities.
On Windows 7 (when using RDP client version 7), this certificate must be installed in the store computer account, to do this, import it through the snap Certificates (local computer) in the MCC console, in the same way as it was done above. Otherwise, the connection will fail and you will receive the following error:
 After installing the CA certificate, you can try to connect, please note that you will be prompted to enter a username and password even before creating an RDP session. If the connection is successful, pay attention to the lock in the window title, which indicates that you are working through SSL. By clicking on it, you can view information about the certificate.
After installing the CA certificate, you can try to connect, please note that you will be prompted to enter a username and password even before creating an RDP session. If the connection is successful, pay attention to the lock in the window title, which indicates that you are working through SSL. By clicking on it, you can view information about the certificate.
And finally, a drop of tar in a barrel of honey. Windows Terminal Services does not know how to authenticate connecting clients, so if necessary, additional security methods should be used, such as an SSH tunnel or IPSec VPN.