Recovery of encrypted files Is a problem faced by a large number of personal computer users who have fallen prey to various ransomware viruses. The number of malicious programs in this group is very large and it is increasing every day. Only recently, we have come across dozens of encryption options: CryptoLocker, Crypt0l0cker, Alpha Crypt, TeslaCrypt, CoinVault, Bit Crypt, CTB-Locker, TorrentLocker, HydraCrypt, better_call_saul, crittt, etc.
Of course, you can restore encrypted files simply by following the instructions that the creators of the virus leave on the infected computer. But most often the cost of decryption is very significant, you also need to know that some ransomware viruses encrypt files so that it is simply impossible to decrypt them later. And of course, it's just frustrating to pay to recover your own files.
Ways to Recover Encrypted Files for Free
There are several ways to recover encrypted files using absolutely free and proven programs such as ShadowExplorer and PhotoRec. Before and during recovery, try to use the infected computer as little as possible, so you increase your chances of successful file recovery.
The instructions described below must be followed step by step, if something does not work out for you, then STOP, ask for help by writing a comment on this article or by creating a new topic on ours.
1. Remove ransomware virus
Kaspersky Virus Removal Tool and Malwarebytes Anti-malware can detect different types of active ransomware viruses and easily remove them from your computer, BUT they cannot recover encrypted files.
1.1. Remove ransomware virus using Kaspersky Virus Removal Tool

Click on the button Scan to start a scan of your computer for the ransomware virus.

Wait until the end of this process and remove the found malware.
1.2. Remove ransomware virus with Malwarebytes Anti-malware
Download the program. After the download is finished, run the downloaded file.


The program update procedure will start automatically. When it's over press the button Run check... Malwarebytes Anti-malware will scan your computer.

Immediately after completing the scan of your computer, Malwarebytes Anti-malware will open a list of the ransomware components found.
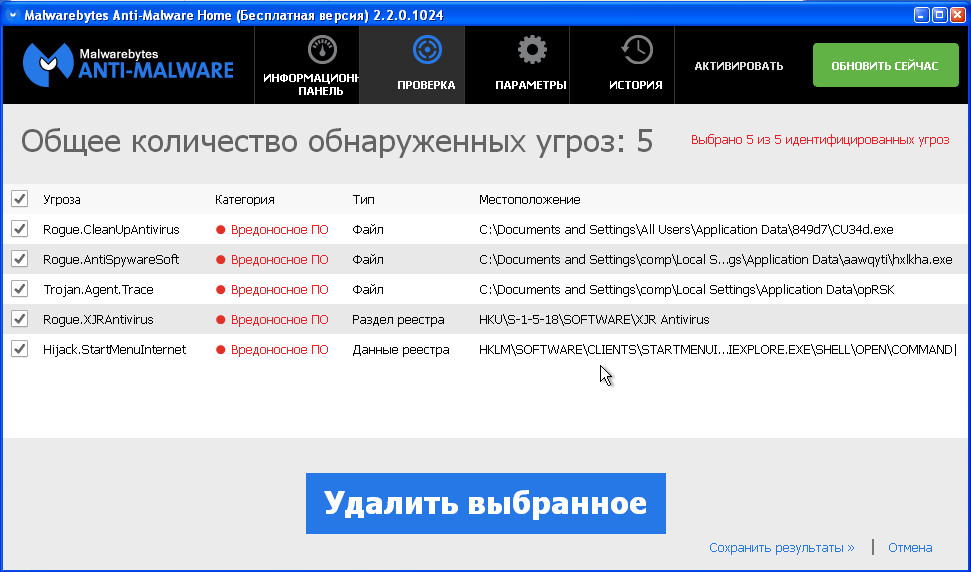
Click on the button Delete selected to clean your computer. During malware removal, Malwarebytes Anti-malware may require you to restart your computer to continue the process. Confirm this by choosing Yes.
Once the computer is restarted, Malwarebytes Anti-malware will automatically continue the cleaning process.
2. Recover encrypted files using ShadowExplorer
ShadowExplorer is a small utility that allows you to restore shadow copies of files that are created automatically by the Windows operating system (7-10). This will allow you to restore the encrypted files to their original state.
Download the program. The program is in a zip archive. Therefore, right-click on the downloaded file and select Extract All. Then open the ShadowExplorerPortable folder.

Start ShadowExplorer. Select the drive you need and the date the shadow copies were created, respectively numbers 1 and 2 in the figure below.

Right-click on the directory or file you want to restore a copy of. Select Export from the menu that appears.

Finally, select the folder where the recovered file will be copied.
3. Recover encrypted files using PhotoRec
PhotoRec is a free program designed to recover deleted and lost files. Using it, you can recover the original files that the ransomware viruses deleted after creating their encrypted copies.
Download the program. The program is in the archive. Therefore, right-click on the downloaded file and select Extract All. Then open the testdisk folder.

Find QPhotoRec_Win in the list of files and run it. The program window will open in which all partitions of the available disks will be shown.

In the list of partitions, select the one containing the encrypted files. Then click on the File Formats button.

By default, the program is configured to recover all types of files, but to speed up the work, it is recommended to leave only the types of files that you need to recover. After completing your selection, click OK.
At the bottom of the QPhotoRec window, find the Browse button and click it. You need to select the directory where the recovered files will be saved. It is advisable to use a disk that does not contain encrypted files requiring recovery (you can use a USB flash drive or an external disk).
To start the procedure for searching and restoring original copies of encrypted files, click the Search button. This process takes quite a long time, so be patient.

When the search is over, click the Quit button. Now open the folder that you chose to save the recovered files.

The folder will contain directories named recup_dir.1, recup_dir.2, recup_dir.3 and so on. The more files the program finds, the more directories there will be. To find the files you need, check all the directories sequentially. To make it easier to find the file you need, among the large number of recovered files, use the built-in Windows search system (by file content), and also do not forget about the function of sorting files in directories. You can select the date the file was modified as the sort option, because QPhotoRec tries to restore this property when restoring the file.
Looking for a program to recover corrupted files? After recovering deleted data, the desired files do not open or open with an error message? Don't know how to recover the structure of damaged photos?
Repair damaged files with the program
Use the program to recover damaged data RS File Repair. The program will quickly fix errors in the file structure and restore them to their original form. A step-by-step recovery wizard and an interface in the style of MS Windows Explorer makes working with the utility easy and intuitive, requiring no special skills. Thanks to this, each user will be able to quickly find and restore the files they need, even after serious damage.
Download Registration ScreenshotsWith RS File Repair, you can "fix" files in two ways.
If you restore data using the wizard, then you can work with several files at once, even if they are in different folders. The program will repair the damage and save the files to the folder of your choice.
If you do not use the wizard when recovering damaged files, then the preview function will be available to you, and you can preview the corrected files before saving.
Recovering damaged files using a wizard
To use a convenient step-by-step wizard to fix and save corrupted files, select Wizard from the File menu.Each new wizard window contains detailed step-by-step instructions to help you recover damaged files with ease. If you want to start working with the wizard every time you start the program, use the option "Display wizard when starting the program".
In the "Select files" window, you need to specify the damaged files that you would like to fix and save. Here you can add any number of files from different folders to the list of recoverable files, delete files from the list, or completely clear the list. You can also choose how to display the list of selected files ("Icons", "List", "Table") and use file sorting.

Then select the type of analysis for the data to be recovered. In most cases, it will be enough to use the "Analysis" function, which allows you to quickly fix the damage to the logical structure of files.
The second type of data processing - "Research" - is used if it is necessary to analyze the file structure in more detail. It takes much longer, but allows you to recover even heavily damaged data by preserving the maximum amount of information in the original files.

In the next window, the wizard will ask you to choose the path to save the recovered data (the folder where they will be saved), as well as to define some more principles for saving the corrected files on the selected medium.

Recover damaged files with preview
If you decided “manually”, without using the wizard, select the folder in the left part of the main program window that contains the files you need. The entire contents of the directory will be displayed on the right, and you can select the files you need in it.
If the file is damaged, the program will not be able to display its contents. To restore its structure, use the "File" - "Analysis" or "File" - "Research" menu of the main program menu. After performing these functions, the files will be available for preview.


Today, perhaps, only a person who is very far from the Internet does not know about the mass infections of computers with the WannaCry ("I want to cry") ransomware Trojan that began on May 12, 2017. And I would divide the reaction of those who know into 2 opposite categories: indifference and panic. What does this mean?
And the fact that fragmentary information does not give a complete understanding of the situation, give rise to speculation and leave behind more questions than answers. In order to understand what is really happening, to whom and what it threatens, how to protect against infection and how to decrypt files corrupted by WannaCry, today's article is devoted.
Is "devil" really so scary
I don't understand what kind of fuss aroundWannaCry? There are many viruses, new ones appear constantly. What's special about this one?
WannaCry (other names WanaCrypt0r, Wana Decrypt0r 2.0, WannaCrypt, WNCRY, WCry) is not an ordinary cyber-malware. The reason for his notoriety is the enormous amount of damage caused. According to Europol, it disrupted the operation of more than 200,000 Windows computers in 150 countries around the world, and the damage suffered by their owners amounted to more than $ 1,000,000,000. And this is only in the first 4 days of distribution. Most of the victims are in Russia and Ukraine.
I know that viruses infiltrate PCs through adult sites. I do not visit such resources, so I am not in danger.
Virus? This is also a problem for me. When viruses start up on my computer, I run the utility *** and after half an hour everything is fine. And if it doesn't help, I reinstall Windows.
Virus to virus - strife. WannaCry is a ransomware Trojan, a network worm capable of spreading over local networks and the Internet from one computer to another without human intervention.
Most malware, including ransomware, starts working only after the user “swallows the bait,” that is, clicks on a link, opens a file, etc. you don't have to do anything to get infected with WannaCry!
Once on a computer with Windows, the malware encrypts the bulk of user files in a short time, after which it displays a message demanding a ransom in the amount of $ 300-600, which must be transferred to the specified wallet within 3 days. In case of delay, he threatens to make decryption of files impossible in 7 days.

At the same time, the malware looks for loopholes to penetrate other computers, and if it finds it, it infects the entire local network. This means that backup copies of files stored on neighboring machines also become unusable.
Removing a virus from your computer does not decrypt files! Reinstalling the operating system is the same. On the contrary, if infected with ransomware, both of these actions can make it impossible for you to recover files even if you have a valid key.
So yes, "devil" is quite scary.
How WannaCry spreads
You're lying. The virus can penetrate my computer only if I download it myself. And I'm alert.
Many malicious programs are able to infect computers (and mobile devices, by the way, too) through vulnerabilities - errors in the code of operating system components and programs that open up the opportunity for cyber-attackers to use a remote machine for their own purposes. WannaCry, in particular, spreads through the 0-day vulnerability in the SMB protocol (zero-day vulnerabilities are errors that were not fixed by malware / spyware at the time of their exploitation).
That is, to infect a computer with an encryption worm, two conditions are sufficient:
- Connections to a network where there are other infected machines (Internet).
- The presence of the above loophole in the system.
Where did this infection come from? Are these the tricks of Russian hackers?
According to some reports (I am not responsible for the accuracy), the US National Security Agency was the first to discover the flaw in the SMB network protocol, which is used for legal remote access to files and printers in Windows. Instead of reporting it to Microsoft in order to fix the bug, the NSA decided to use it themselves and developed an exploit for this (a program that exploits the vulnerability).
 Visualization of WannaCry propagation dynamics on intel.malwaretech.com
Visualization of WannaCry propagation dynamics on intel.malwaretech.com Subsequently, this exploit (codenamed EternalBlue), which served for some time by the NSA to penetrate computers without the knowledge of the owners, was stolen by hackers and formed the basis for the creation of the ransomware WannaCry. That is, thanks to the not entirely legal and ethical actions of the US government, the virus writers learned about the vulnerability.
I disabled the installation of updatesWindows. Nafig is necessary when everything works without them.
The reason for such a rapid and large-scale spread of the epidemic is the absence at that time of a "patch" - a Windows update that could close the Wanna Cry loophole. After all, it took time to develop it.
Today such a patch exists. Users who update the system automatically received it in the first hours after release. And those who believe that updates are unnecessary are still at risk of infection.
Who is at risk of a WannaCry attack and how to defend against it
As far as I know, more than 90% of computers infectedWannaCry, ran under controlWindows 7. I have a ten, which means that nothing threatens me.
All operating systems that use the SMB v1 network protocol are at risk of WannaCry infection. It:
- Windows XP
- Windows Vista
- Windows 7
- Windows 8
- Windows 8.1
- Windows RT 8.1
- Windows 10 v 1511
- Windows 10 v 1607
- Windows Server 2003
- Windows Server 2008
- Windows Server 2012
- Windows Server 2016
Users of systems on which they have not been installed are at risk of picking up malware over the network. critical Security Update MS17-010 (available for free download from technet.microsoft.com, which is linked). Patches for Windows XP, Windows Server 2003, Windows 8 and other unsupported OS can be downloaded from this page support.microsoft.com ... It also describes how to check for a rescue update.
If you don't know the OS version on your computer, press the Win + R key combination and run the winver command.

To strengthen protection, as well as if it is impossible to update the system now, Microsoft provides instructions for temporarily disabling the SMB version 1 protocol. They are located and. Additionally, but not necessarily, you can close the TCP port that serves SMB through firewall 445.
I have the best antivirus in the world ***, with it I can do anything and I am not afraid of anything.
WannaCry can spread not only by the above-described self-propagation, but also in the usual ways - via social networks, email, infected and phishing web resources, etc. And there are such cases. If you download and run the malicious program manually, then neither antivirus nor patches that close vulnerabilities will save you from infection.
How does the virus work, what does it encrypt
Yes, let him encrypt what he wants. My friend is a programmer, he will decipher everything for me. As a last resort, we will find the key by brute force.
Well, it will encrypt a couple of files, so what? It won't stop me from working on my computer.
Unfortunately, it will not decrypt, because there are no ways to break the RSA-2048 encryption algorithm that Wanna Cry uses and will not appear in the foreseeable future. And it will not encrypt a couple of files, but almost everything.
I will not give a detailed description of the malware's work, anyone interested can get acquainted with its analysis, for example, in the blog of Microsoft expert Matt Suiche. I will mention only the most significant moments.
Files with the following extensions are encrypted: .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pst, .ost, .msg, .eml, .vsd, .vsdx, .txt, .csv, .rtf, .123, .wks , .wk1, .pdf, .dwg, .onetoc2, .snt, .jpeg, .jpg, .docb, .docm, .dot, .dotm, .dotx, .xlsm, .xlsb, .xlw, .xlt,. xlm, .xlc, .xltx, .xltm, .pptm, .pot, .pps, .ppsm, .ppsx, .ppam, .potx, .potm, .edb, .hwp, .602, .sxi, .sti, .sldx, .sldm, .sldm, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .bz2, .tbk, .bak, .tar, .tgz, .gz, .7z , .rar, .zip, .backup, .iso, .vcd, .bmp, .png, .gif, .raw, .cgm, .tif, .tiff, .nef, .psd, .ai, .svg,. djvu, .m4u, .m3u, .mid, .wma, .flv, .3g2, .mkv, .3gp, .mp4, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .mp3, .sh, .class, .jar, .java, .rb, .asp, .php, .jsp, .brd, .sch, .dch, .dip, .pl , .vb, .vbs, .ps1, .bat, .cmd, .js, .asm, .h, .pas, .cpp, .c, .cs, .suo, .sln, .ldf, .mdf,. ibd, .myi, .myd, .frm, .odb, .dbf, .db, .mdb, .accdb, .sql, .sqlitedb, .sqlite3, .asc, .lay6, .lay, .mml, .sxm, .otg, .odg, .uop, .std, .sxd, .otp, .odp, .wb2, .slk, .dif, .stc, .sxc, .ots, .ods, .3dm, .max, .3ds, .uot, .stw, .sxw, .ott, .odt, .pem, .p12, .csr, .crt, .key, .pfx , .der.
As you can see, there are documents, photos, video and audio, archives, mail, and files created in various programs ... The malware tries to reach every directory on the system.
Encrypted objects get double expansion with the postscript WNCRY, for example, "Document1.doc.WNCRY".

After encryption, the virus copies an executable file to each folder @[email protected] - ostensibly for decryption after ransom, as well as a text document @[email protected] with a message to the user.
Next, it tries to wipe out shadow copies and Windows restore points. If the system is running UAC, the user must confirm this operation. If you deny the request, there will be a chance to restore the data from the copies.
WannaCry transmits the encryption keys of the affected system to command centers located in the Tor network, and then deletes them from the computer. To find other vulnerable machines, it scans the local network and arbitrary IP ranges on the Internet, and once found, it penetrates everything it can get to.
Today, analysts are aware of several modifications of WannaCry with different distribution mechanisms, and in the near future, we should expect new ones to appear.
What to do if WannaCry has already infected your computer
I can see the files change extensions. What's happening? How do you stop this?
Encryption is not a one-step process, although not too long. If you managed to notice it before the ransomware message appears on the screen, you can save some of the files by immediately turning off the computer power. Not shutting down the system, but by pulling out the plug!
When you boot Windows in normal mode, encryption will continue, so it is important to prevent it. The next start of the computer should occur either in safe mode, in which viruses are not active, or from another bootable media.
My files are encrypted! The virus demands a ransom for them! What to do, how to decrypt?
Decryption of files after WannaCry is possible only if there is a secret key, which the attackers promise to provide as soon as the victim transfers them the ransom amount. However, such promises are almost never fulfilled: why should the malware distributors bother if they already got what they wanted?
In some cases, the problem can be solved without a ransom. To date, 2 WannaCry decoders have been developed: WannaKey(by Adrien Guinet) and WanaKiwi(by Benjamin Delpy). The first works only in Windows XP, and the second, created on the basis of the first, - in Windows XP, Vista and 7 x86, as well as in northern systems 2003, 2008 and 2008R2 x86.
The algorithm of operation of both decryptors is based on the search for secret keys in the memory of the encryption process. This means that only those who did not have time to restart their computer have a chance to decrypt. And if not too much time has passed after encryption (the memory has not been overwritten by another process).
So, if you are a Windows XP-7 x86 user, the first thing to do after the ransom message appears is to disconnect the computer from the local network and the Internet and run the WanaKiwi decryptor downloaded on another device. Do not perform any other actions on the computer before removing the key!
You can read the description of the work of the WanaKiwi decryptor in another blog by Matt Suiche.
After decrypting the files, run an antivirus to remove the malware and install a patch that closes its distribution paths.
Today, WannaCry recognizes almost all antivirus programs except those that are not updated, so almost any will do.

How to live this life further
The self-propelled epidemic took the world by surprise. For all kinds of security services, it turned out to be as unexpected as the onset of winter on December 1 for public utilities. The reason is carelessness and maybe. The consequences are irreparable loss of data and damages. And for the creators of malware - an incentive to continue in the same spirit.According to analysts, WanaCry has paid distributors very good dividends, which means that attacks like this will be repeated. And those who are carried away now will not necessarily be carried away later. Of course, if you don't worry about it in advance.
So, so that you don't ever have to cry over encrypted files:
- Do not refuse to install updates to the operating system and applications. This will protect you from 99% of threats that spread through unpatched vulnerabilities.
- Keep on.
- Create backup copies of important files and store them on another physical medium, or better - on several. In corporate networks, it is optimal to use distributed storage databases; home users can adopt free cloud services like Yandex Drive, Google Drive, OneDrive, MEGASynk, etc. Do not keep these applications running when you are not using them.
- Choose reliable operating systems. Windows XP is not.
- Install a comprehensive anti-virus of the Internet Security class and additional protection against ransomware, for example, Kaspersky Endpoint Security. Or analogues of other developers.
- Improve your literacy level in countering Trojan-ransomware. For example, the anti-virus vendor Dr.Web has prepared training courses for users and administrators of various systems. A lot of useful and, importantly, reliable information is contained in the blogs of other A / V developers.
And most importantly: even if you have suffered, do not transfer money to cybercriminals for decryption. The probability that you will be deceived is 99%. Besides, if no one pays, the extortion business will become meaningless. Otherwise, the spread of such an infection will only grow.
Not so long ago, a new virus (and many of its modifications) appeared on the Internet, encrypting files on your computer and offering to order a program for their decryption for money. This renames the encrypted files and gets names like this
DSC00122.JPG. [email protected]_XO101
The highlighted part consists of the e-mail of the author of the virus (to which the "victim" of the virus will send a request for decryption) and the identifier of the virus modification. Each modification of the virus has its own encryption algorithm and, accordingly, requires its own decryptor.
Fortunately, the Dr.Web developers have taken up this issue closely and are ready to provide a special utility that decrypts files corrupted by a virus. For convenience, below I post the utility itself and a brief instruction on its use.
(password is the name of my site without "http: //")
Below is a brief instruction.
Download the recovery utility, unpack the archive into an empty folder with a simple name (for example, “ C: \\ _ dec"). Then start the command line (Start - Run - cmd) and type the following there:
Here " [email protected]_XO101"Is the prefix with which the virus renamed your files, pay attention to the dot at the beginning. AND c: \\ myfiles \\ Is the folder that contains your encoded files. After starting the program will open a confirmation window

And after clicking on the "Continue" button, automatic treatment will begin. Upon completion of the program, you will receive a report, and all the decoded files will lie next to the encoded ones in the folder you specified (the program does not delete encoded versions of files).

The authors of the program do not guarantee 100% cure of all files, and I have no opportunity to check its work on a large number of files, so please: whoever managed to cure files with this utility (or did not succeed) - please write in the comments.
That's all! Be healthy!
P.S. And so that the situation with computer infection does not repeat itself again, purchase already normal antivirus... I use Kaspersky Internet Security, but Dr.Web seems to be good too. Believe my experience, one and a half thousand rubles a year for peace of mind and confidence in the future is a ridiculous price.
A virus is a type of malicious software that penetrates system memory areas, code of other programs, and boot sectors. It is capable of deleting important data from a hard drive, USB drive or memory card.
Most users do not know how to recover files after a virus attack. In this article, we want to tell you how to do it in a quick and easy way. We hope that this information will be useful to you. There are two main methods you can use to easily remove the virus and recover deleted data after a virus attack.
Delete the virus using the command prompt
1) Click the “Start” button. Enter CMD in the search bar. You will see the “Command Prompt” at the top of the pop-up window. Press Enter.
2) Run the Command prompt and type in: “attrib –h –r –s / s / d driver_name \\ *. *”

After this step, Windows will start recovering the virus-infected hard drive, memory card or USB. It will take some time for the process to be completed.
To start Windows recovery, click the “Start” button. Type Restore in the search bar. In the next window click “Start System Restore” → “Next” and select the desired restore point.

Another variant of the path is “Control Panel” → “System” → “System Protection”. A recovery preparation window will appear. Then the computer will reboot and a message will appear saying “System Restore completed successfully.” If it did not solve your problem, then try rolling back to another restore point. That’s all to be said about the second method.
Magic Partition Recovery: Restoring Missing Files and Folders after a Virus Attack
For reliable recovery of files deleted by viruses, use Magic Partition Recovery. The program is based on direct low-level access to the disk. Therefore, it will bypass the virus blocking and read all your files.
Download and install the program, then analyze the disk, flash drive or memory card. After the analysis, the program displays the list of folders on the selected disk. Having selected the necessary folder on the left, you can view it in the right section.

Thus, the program provides the ability to view the contents of the disk in the same way as with the standard Windows Explorer. In addition to existing files, deleted files and folders will be displayed. They will be marked with a special red cross, making it much easier to recover deleted files.
If you have lost your files after virus attack, Magic Partition Recovery will help you restore everything without much effort.