Not long ago, a new virus (and many of its modifications) appeared on the Internet, encrypting files on your computer and offering to order a program to decrypt them for money. In this case, the encrypted files are renamed and given names like this
DSC00122.JPG. [email protected] _XO101
The selected part consists of the e-mail of the virus author (to which the “victim” of the virus will send a decryption request) and the virus modification identifier. Each modification of the virus has its own encryption algorithm and, accordingly, requires its own decryptor.
Fortunately, the developers from Dr.Web have taken up this issue closely and are ready to provide a special utility that decrypts files corrupted by the virus. For convenience, below I post the utility itself and brief instructions for using it.
(password is the name of my site without “http://”)
Below are brief instructions.
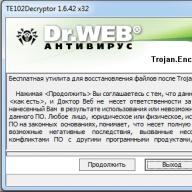
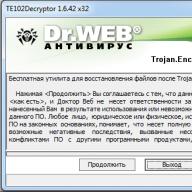
Download the recovery utility, unpack the archive into an empty folder with a simple name (for example, “ C:\_dec"). Then open the command line (Start - Run - cmd) and type the following there:
Here " [email protected] _XO101" is the prefix with which your files are renamed by the virus, pay attention to the dot at the beginning. A c:\myfiles\- this is the folder in which your encoded files are located. After launching the program will open a confirmation window

And after clicking on the “Continue” button, automatic treatment will begin. Upon completion of the program, you will receive a report, and all decoded files will be located next to the encoded ones in the folder you specified (the program does not delete encoded versions of files).

The authors of the program do not guarantee 100% treatment of all files, and I do not have the opportunity to test its operation on a large number of files, so please: whoever managed to cure files with this utility (or did not succeed) - write in the comments.
That's all! Be healthy!
P.S. To prevent the situation of your computer becoming infected from happening again, purchase it already normal antivirus. I use Kaspersky Internet Security, but apparently Dr.Web is also quite good. Believe me, one and a half thousand rubles a year for peace of mind and confidence in the future is a ridiculous price.
A virus on a flash drive is no surprise to anyone. But being left without important information that is stored on this very flash drive is another incident. My friends have formatted flash drives more than once after viruses, without finding a single file there. And they may simply be hidden by a virus... As they say in our business, it’s better to be safe than sorry. And so... The virus on the flash drive was cured or deleted. We enter the root directory, and it’s empty. What should I do? I have not encountered viruses that would impudently erase information from storage devices. So most likely your files are hidden. Which means we need to show them.
Show hidden files and folders.
To show hidden files. In any window press the button Service
Then select Folder properties...

Tab View


And press OK
After this, all hidden files and folders will be displayed. And if you're lucky, you can simply uncheck the hidden attribute in the properties of a folder or document. To do this, right-click on the desired document or folder and select Properties. Then uncheck the attribute Hidden.
But it may be that it will be impossible to remove this file attribute or, even worse, Files and folders on the flash drive will not be displayed at all. Then, let's resort to the command line.
Open the command line.
To do this, press the key combination Win+R. We get a window with the name Execute.
In the input field we write cmd

and press OK
In the command line, go to our flash drive.
Enter X:(Where X is the letter of your flash drive or disk) and press Enter
After that we enter attrib -s -h -r -a /s /d, press again Enter
That's all. Now the attribute Hidden will be deleted from all files and folders on your flash drive. Accordingly, all data will be displayed as expected. Unless of course they are there.
Recovering hidden files after a virus is a common problem that PC users have to face. Recently, many people have been suffering from malware, due to which all files and folders on the hard drive are lost, including personal content like documents, images, etc. Malware can also hide all shortcuts in the Start menu. The virus does not delete data, but adds a hidden attribute to all files and folders on your system, and as a result, it appears as if all data has been deleted from the hard drive.
If you need to perform file recovery after a virus, you can use the instructions below to redisplay all the data that was missing and regain control of your computer. In case the operating system is still infected with malware, you need to use antivirus software. Once the viruses are removed, you can begin to take steps to display the files and folders that have disappeared. To display missing files, you need to change your Windows system settings.
How to show hidden files
If you are running Windows XP, you can recover lost data by doing the following:
- open My Computer;
- select Tools;
- click on Folder Options;
- select the View tab;
- check the box next to the Show Hidden Files and Folders option;
- Click OK to return lost data from your hard drive or flash drives.
To recover data that was lost on Windows Vista, you need to follow these steps:
- press the Start button;
- select Computer;
- click on Tools;
- select Folder Options;
- use the View button;
- select the Show Hidden Files and Folders option;
- click OK.
If you are interested in how to recover hidden files on Windows 7, you need to follow these steps:
- press the Start button;
- select Computer;
- click Organize;
- use the Folder and Search Options button;
- select View;
- activate the Show Hidden Files and Folders option;
- click OK.
After completing the above steps, you will be able to see all your files and folders for office programs and other applications, but they will still contain a hidden set of attributes. If you delete unnecessary parameters for files on a flash drive or hard drive, then all of them will be displayed in normal mode.
How to remove hidden attributes
If you are using the Windows XP operating system, you need to perform the following steps:
- Click Start and Run.
- Type cmd and press Enter.
- In the command line, type CD\ and confirm with the Enter key.
- Type ATTRIB -H *.* /S /D and press Enter. This command will display files that have become invisible. Since important system files have the corresponding attribute attached, the above command will not affect them. System settings let them through and hide them from prying eyes, so your most important content isn't lost. The command will take some time to complete, so don't worry if the process takes a few minutes or even half an hour. The command will perform simple actions - it will remove hidden attributes from all directories on the hard drive and folders on the flash drive after the virus. The /S parameter means that the current folder and all its subdirectories will be searched. The /D option processes all other folders.
For Windows Vista or 7 you need to do the following:
- Click Start and All Programs.
- Select Accessories and Find Command Prompt.
- Right-click on the Command Prompt option and select Run as Administrator.
- At the command line, type CD\ and press Enter.
- The command line should now indicate the root folder of the hard drive (probably C:\).
- Type ATTRIB -H *.* /S /D and press Enter.
- Type Exit and press Enter when the procedure is complete. To restart a computer.
An alternative is to use the Unhide app created by Bleeping Computer. This is a program for recovering hidden files from flash drives and hard drives. On the official website of this developer there is a whole tutorial on using unhide.exe to delete deleted data after a virus invasion. With its help, users received the necessary information and successfully restored their PCs. You can download this application for hidden folders and files on your desktop and run it so that the above steps to remove attributes from a flash drive after a virus will be performed automatically by the system.
Fix problems with shortcuts on the taskbar and Start menu
To display shortcuts on the taskbar and in the Start menu after a virus attack, you need to do the following:
- Open Computer.
- Go to Drive C, Users, Your User Name, AppData, Local, Temp, SNTMP or SMTMP.
- Open the directory with number 1.
- Select Edit, Select All and Copy.
- Leave the directory open and go to My Computer again.
- Select Drive C, Program Data, Microsoft, Windows, Start Menu.
- Click Edit and Paste to copy the Programs folder and other shortcuts to the appropriate location.
- Open the directory with the number 3.
- Select all files and copy them.
- Go to Drive C, Users, Username, AppData, Roaming, Microsoft, Internet Explorer, Quick Launch, User Pinned, Taskbar and paste files.
After completing the above steps, all shortcuts should return to their places.
Are you looking for a program to recover damaged files? After recovering deleted data, the necessary files do not open or open with an error message? Don't know how to restore the structure of damaged photos?
Recover damaged files with the program
Use RS File Repair to recover damaged data. The program will quickly correct errors in the file structure and restore them to their original form. The step-by-step recovery wizard and MS Windows Explorer-style interface make working with the utility easy and straightforward, not requiring special skills. Thanks to this, each user will be able to quickly find and restore the necessary files even after serious damage.
Download Registration ScreenshotsWith RS File Repair you can "fix" files in two ways.
If you restore data using the wizard, you will be able to work with several files at once, even if they are in different folders. The program will repair the damage and save the files to the folder of your choice.
If you do not use the wizard when restoring damaged files, then the preview function will be available to you, and you will be able to preview the corrected files before saving.
Recovering damaged files using the wizard
To use a convenient step-by-step wizard to fix and save damaged files, select "Wizard" from the "File" menu.In each new wizard window, you will find detailed step-by-step instructions that will help you easily recover damaged files. If you want to start working with the wizard every time you start the program, use the “Display the wizard when starting the program” option.
In the "Select Files" window, you need to indicate the damaged files that you would like to fix and save. Here you can add any number of files from different folders to the list of recoverable ones, remove files from the list, or completely clear the list. You can also choose how to display the list of selected files (“Icons”, “List”, “Table”) and use file sorting.

Then select the type of analysis for the recovered data. In most cases, it will be enough to use the “Analysis” function, which allows you to quickly eliminate damage to the logical structure of files.
The second type of data processing – “Research” – is used if it is necessary to analyze the file structure in more detail. This takes much more time, but allows you to recover even severely damaged data by preserving the maximum amount of information from the original files.

In the next window, the wizard will prompt you to select the path to save the recovered data (the folder in which it will be saved), and also determine some more principles for saving the corrected files on the selected media.

Recover damaged files with preview
If you decide “manually”, without using a wizard, select the folder in which the files you need are located on the left side of the main program window. The entire contents of the directory will be displayed on the right, and you can select the files you need in it.
If the file is damaged, the program will not be able to display its contents. To restore its structure, use the menu “File” - “Analysis” or “File” - “Research” of the main menu of the program. After completing these functions, the files will be available for preview.


Traveling to different cities and towns, a person willy-nilly encounters surprises that can be both pleasant and provoke increased discomfort and severe grief.
The same emotions can await a user who is interested in “travelling” on the Internet. Although sometimes unpleasant surprises fly into email on their own in the form of threatening letters and documents, which users try to read as soon as possible, thereby falling into the networks of scammers.
On the Internet, you can encounter an incredible number of viruses programmed to perform multiple negative tasks on your computer, so it is important to learn to distinguish between safe links for downloading files and documents and avoid those that pose a clear danger to your computer.
If you have become one of those unfortunate people who had to experience the negative consequences of a virus intervention, you will not doubt that it is useful to collect and subsequently systematize information on how to prevent infection of your computer.
Viruses appeared as soon as computer technology appeared. Every year there are more and more varieties of viruses, so it is easy for the user to destroy only the virus carrier that has long been known, and a 100% method of its destruction has been found.
It is much more difficult for the user to “fight” against virus carriers that just appear on the network or are accompanied by full-scale destructive actions.
File recovery methods
In a situation where a virus has encrypted files on a computer, what to do is a key question for many. If these are amateur photos, the loss of which you also don’t want to accept, you can look for ways to solve the problem over a long period of time. However, if a virus has encrypted files that are extremely important for business activities, the desire to figure out what to do becomes incredibly large, and you also want to take effective steps quickly enough.
Restoring a previous version
If system protection was turned on on your computer in advance, then even in cases where an “uninvited guest encryptor” has already managed to take over you, you will still be able to restore documents, knowing what to do in this case.
The system will help you recover documents using their shadow copies. Of course, the Trojan also directs its efforts to eliminate such copies, but viruses are not always able to carry out such manipulations, since they do not have administrative rights.
Step 1
So, it’s easy to restore a document using its previous copy. To do this, you right-click on the file that turns out to be damaged. In the menu that appears, select “Properties”. A window will appear on your PC screen with four tabs, you need to go to the last tab “Previous Versions”.

Step 2
All available shadow copies of the document will be listed in the window below; all you have to do is select the option that is most suitable for you, then click on the “Restore” button.
Unfortunately, such “ambulance” cannot be used on a computer where system protection has not been enabled in advance. For this reason, we recommend that you turn it on in advance, so as not to “bite your elbows” later, reproaching yourself with obvious disobedience.
Step 3
It’s also easy to enable system protection on your computer; it won’t take much of your time. Therefore, banish your laziness and stubbornness and help your computer become less vulnerable to Trojans.
Right-click on the “Computer” icon and select “Properties”. On the left side of the window that opens there will be a list in which find the line “System protection”, click on it.
Now a window will open again in which you will be asked to select a disk. With local drive “C” selected, click the “Configure” button.

Step 4
Now a window will open offering recovery options. You need to agree with the first option, which involves restoring system settings and previous versions of documents. Finally, click the traditional “Ok” button.
If you have done all these manipulations in advance, then even if a Trojan visits your computer and encrypts your files, you will have excellent prospects for recovering important information.
At least you won’t panic when you discover that all the files on your computer are encrypted; in this case, you will already know exactly what to do.
Using Utilities
Many antivirus companies do not leave users alone with the problem of viruses encrypting documents. Kaspersky Lab and Doctor Web have developed special utilities to help resolve such problematic situations.
So, if you find terrible traces of a ransomware visit, try using the Kaspersky RectorDecryptor utility.
Run the utility on your computer, specify the path to the file that was encrypted. It is not difficult to understand what the utility should do directly. Using multiple options, it tries to find the key to decrypt the file. Unfortunately, such an operation can be quite lengthy and is not within the time frame for many users.

In particular, it may happen that it takes about 120 days to select the correct key. At the same time, you must understand that it is not recommended to interrupt the decryption process, so you should also not turn off the computer.
Kaspersky Lab also offers other utilities:
- XoristDecryptor;
- RakhniDecryptor;
- Ransomware Decryptor.
These utilities are aimed at the results of the malicious activities of other ransomware Trojans. In particular, the Ransomware Decryptor utility is still unknown to many, since it is aimed at combating CoinVault, which is only now beginning to attack the Internet and penetrate users’ computers.
Doctor Web developers are also not idle, so they present users with their utilities, with which you can also try to recover encrypted documents on your computer.
Create any folder on drive C and give it a simple name. Unzip the utility downloaded from the company’s official website into this folder.
Now you can use it to practically solve the problem. To do this, launch a command line, type “cd c:\XXX” in it, where instead of XXX enter the name of the folder in which you placed the utility.

Instead of “myfiles” the name of the folder in which the damaged documents are located should be written.
Now the utility will launch and the treatment process will begin; after successful completion, you will find a report indicating what was recovered. By the way, the program does not delete encrypted files, but simply saves the recovered version next to them.
Unfortunately, even this Doctor Web utility cannot be considered as a magic wand; it also cannot do everything.
Many may have already figured out what to do in the event of an infection, but experienced users recommend obtaining information on what is strictly not recommended to do, so as not to provoke more serious consequences when the chances of document recovery are zero.
You cannot reinstall the operating system on your computer. In this case, you may be able to eliminate the pest, but you will definitely not be able to return the documents to working condition.
You cannot run programs that are responsible for cleaning the registry or deleting temporary files on the computer.
It is not recommended to perform anti-virus scanning, during which infected documents can simply be deleted. If you were a little stupid and launched an antivirus, succumbing to panic, then at least make sure that all infected files are not deleted, but simply quarantined.
If you are an advanced user, you can interrupt the encryption process on your computer before it spreads to all files and documents. To do this, you need to launch the “Task Manager” and stop the process. An inexperienced user is unlikely to be able to figure out which process is related to the virus.
It is useful to disconnect your computer from the Internet. By breaking such a connection, the process of encrypting files and documents on the computer in most cases is also interrupted.
So, with a full understanding of what to do when a ransomware Trojan is detected, you can take steps to ensure success. In addition, having received information on how to decrypt files encrypted by a virus, you can try to eliminate the problem yourself and prevent it from occurring again.